CLOUDANIX
Code Security - Bake in security from your PR
Protect Your Fintech Solutions With Cloudanix
Key Challenges in Code Security
Challenges in Early Code Security You Shouldn’t Ignore
Code security challenges start from the very first line of code. If not tackled early in the Software Development Life Cycle (SDLC), they can create long-term risks. A reliable security solution should help teams improve visibility, support multiple tools, and prioritize risks effectively.
Visibility
Real-time scanning helps provide the visibility teams need to maintain code sanity and keep vulnerabilities out.
Tool Coverage
The tool should support popular coding languages and CI/CD tools to be adopted by diverse developer teams proficient in various stacks.
Prioritize Risks
A good tool must provide actionable insights that prioritize risks by severity, enabling teams to fix the most critical issues first—saving time and boosting productivity.
Trusted by thousands of companies worldwide
Cloudanix
Cloudanix Approach to Code Security
Cloudanix ensures your code remains secure from pull request to production. Our platform addresses the modern security needs of fast-moving dev teams—without the friction.
Security from PR to Runtime
Investing in tools that provide multi-faceted security like SAST, DAST, SCA, IAST, Database Scanning, ASTaaS, and other complicated jargon has become a norm. But do you need all this? Cloudanix provides correlation right from PR to runtime, eliminating the need for some of these capabilities like DAST, which is notorious for consuming high compute of your system while providing you the security your code requires. As mentioned above, Cloudanix understands, that new tools and processes are difficult to adopt in organizations and can cause friction. Our Zero Friction philosophy helps us build our platform so that Security teams, DevOps teams and the Engineering teams stay on the same page and align from Day 1 when it comes to Code-To-Cloud security.
Achieve Zero Friction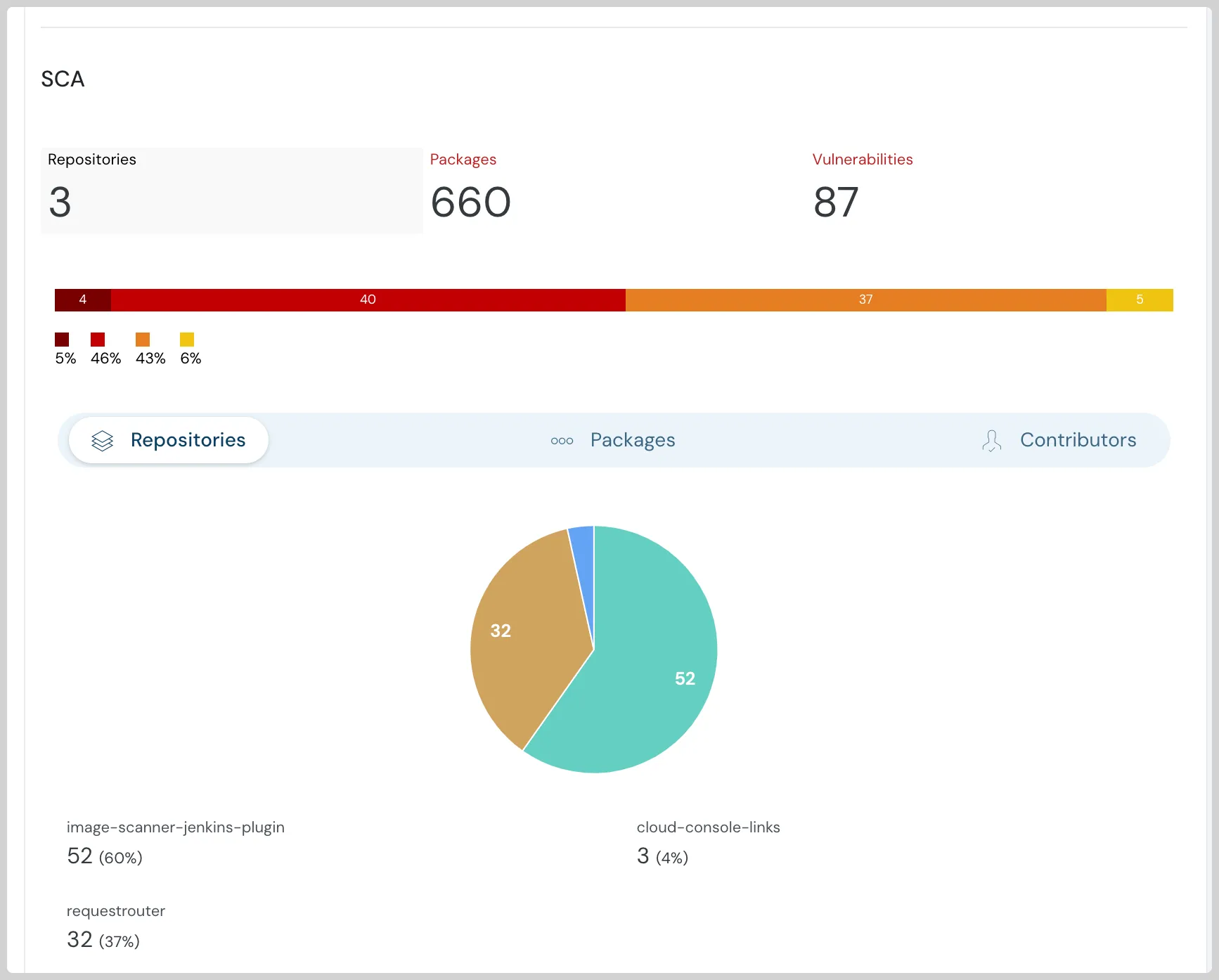
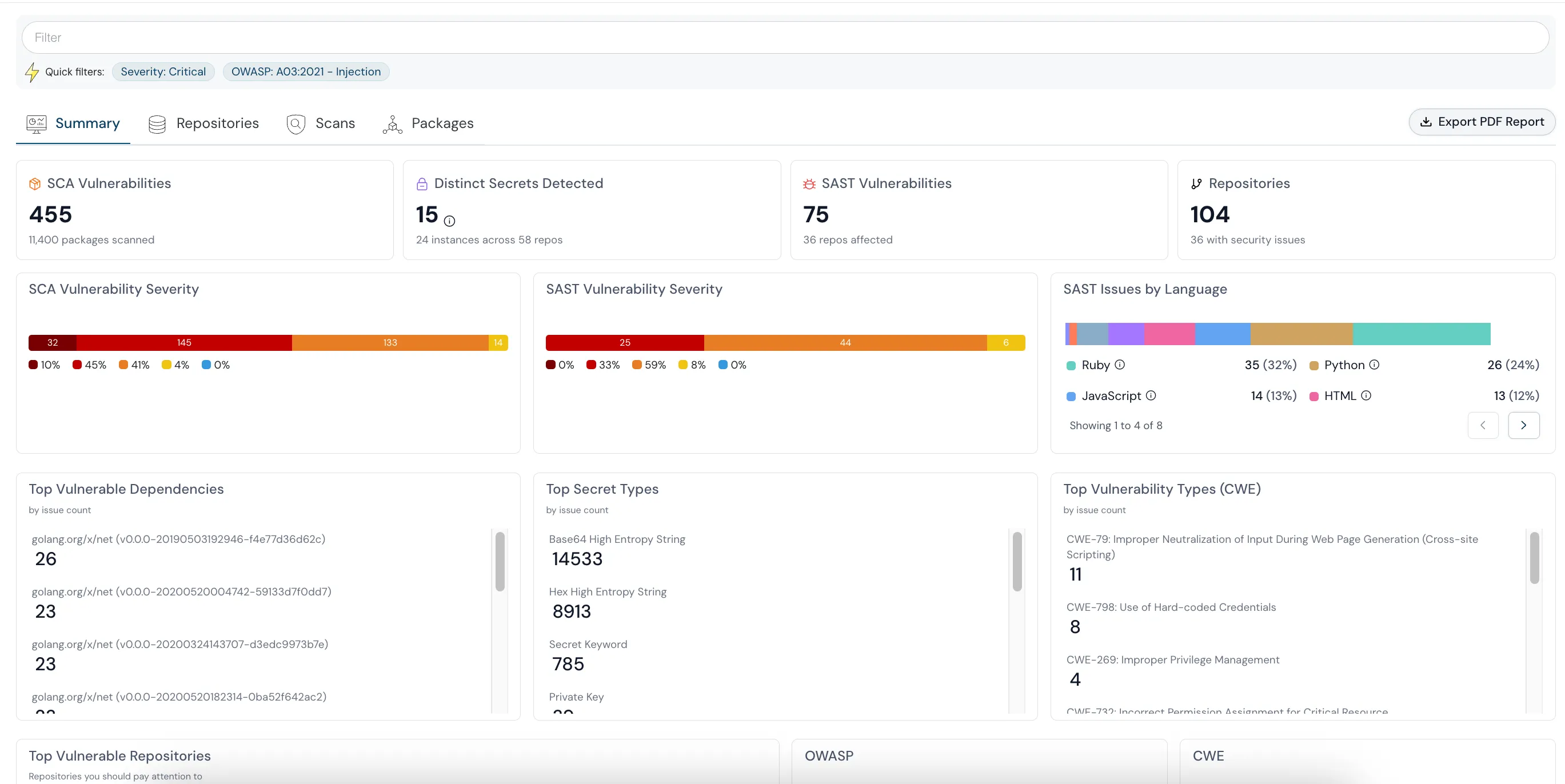
Identify and Address Vulnerabilities in your Open Source dependencies
Cloudanix SCA helps Identify Vulnerabilities and Compliance Issues (License, Maintenance, Security Practices, etc.). Automatically scan your Code Repositories for Software Bill Of Materials (SBOM) and find out Vulnerabilities, Compliance Issues associated with the SBOM for Supply Chain Security.
Explore Cloudanix SCA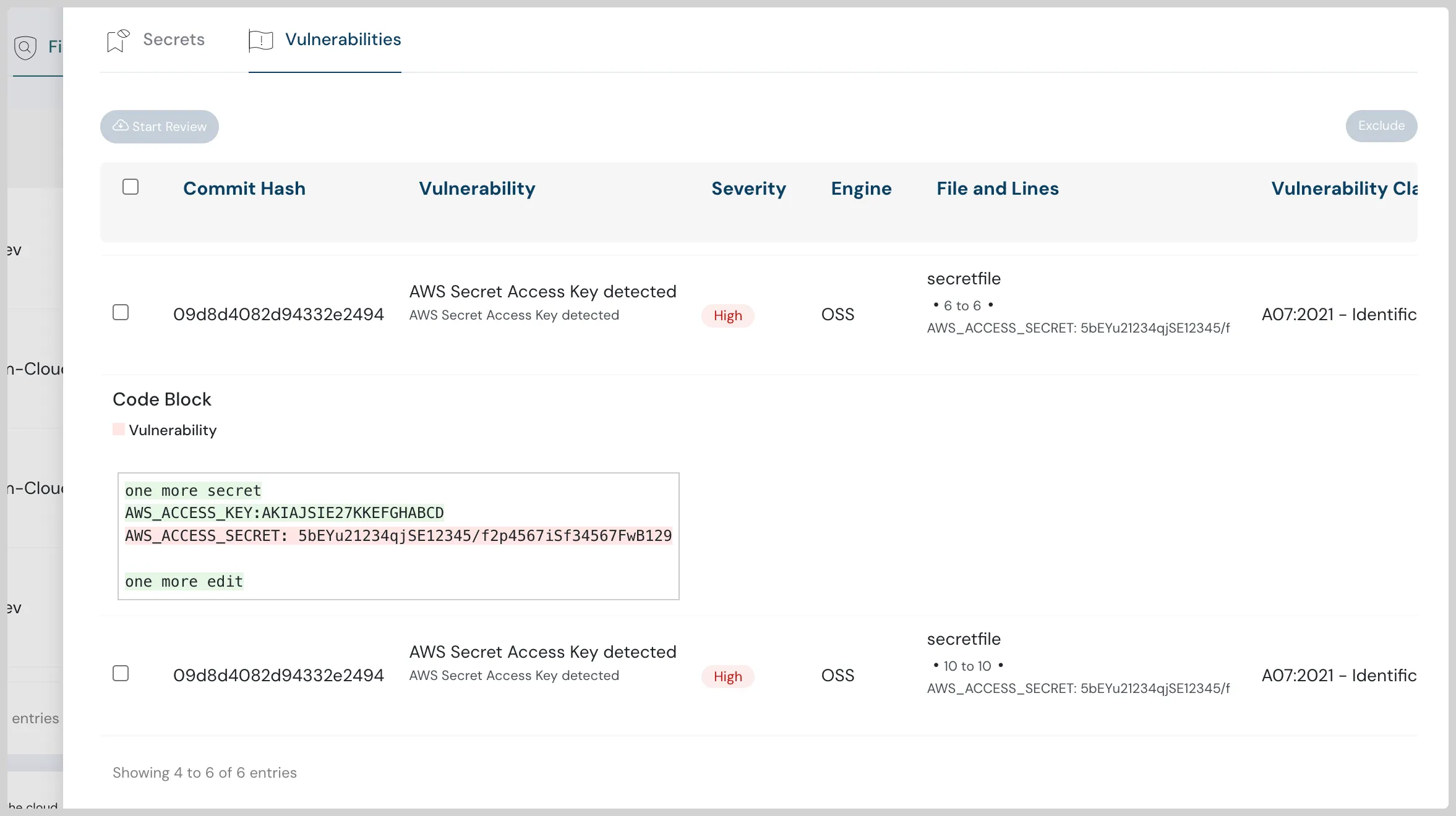
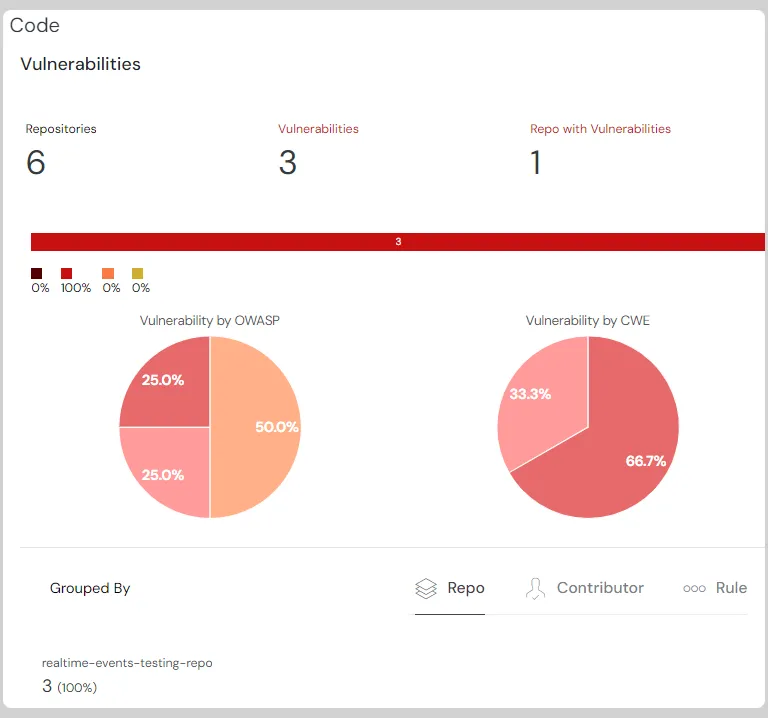
Code Blocks and Workflows
Code Security is now extended by showing Code Blocks affected by Vulnerabilities and also enables you to Triage them by using Review Capability. Review Capability includes “Pause”, “Acknowledge” and “Accept Risk” options.
Explore Cloudanix SASTCLOUDANIX
Cloudanix Code Security for you
Cloudanix delivers exceptional code security for your crown jewels from PR to runtime.
PR Check
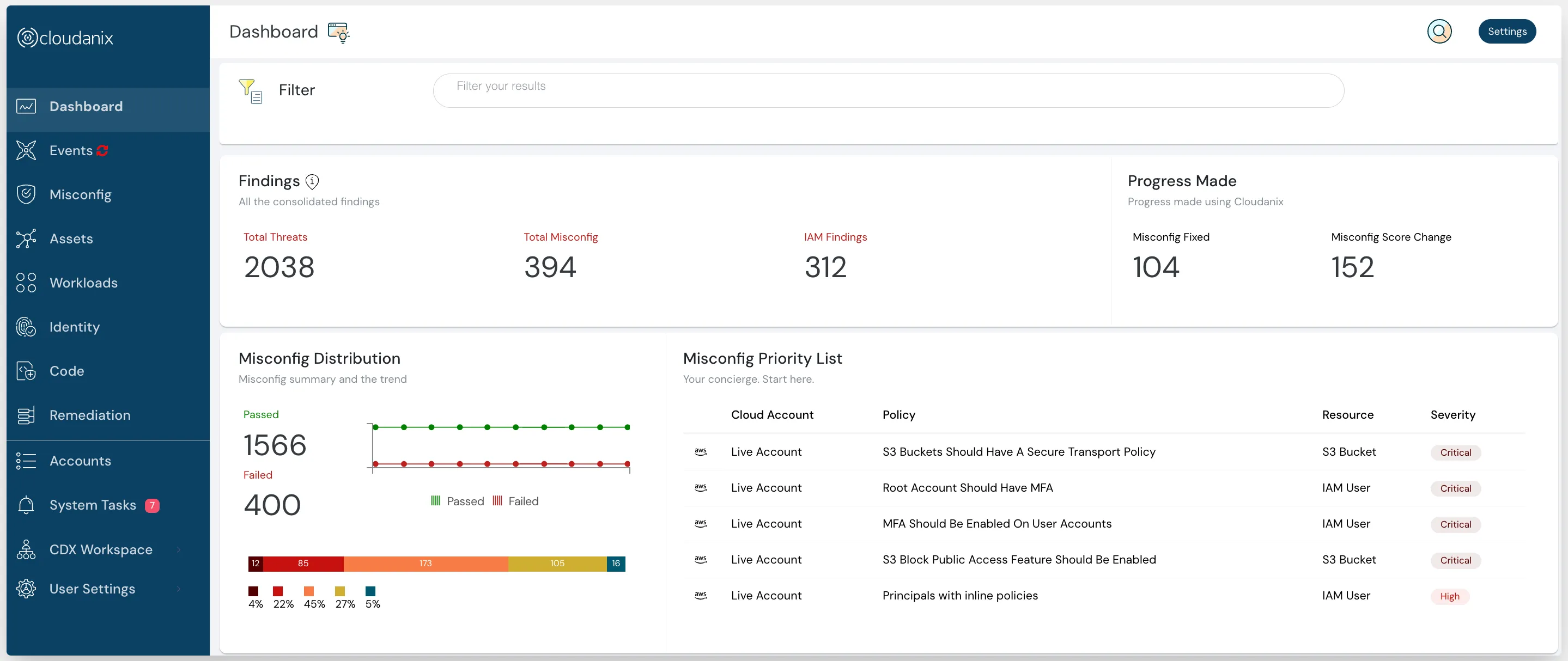
Cloudanix proactively safeguards your codebase against potential security issues by automatic real-time scans of code changes immediately upon the submission of a pull request (PR). Dashboard: Security posture Dashboard: Security posture
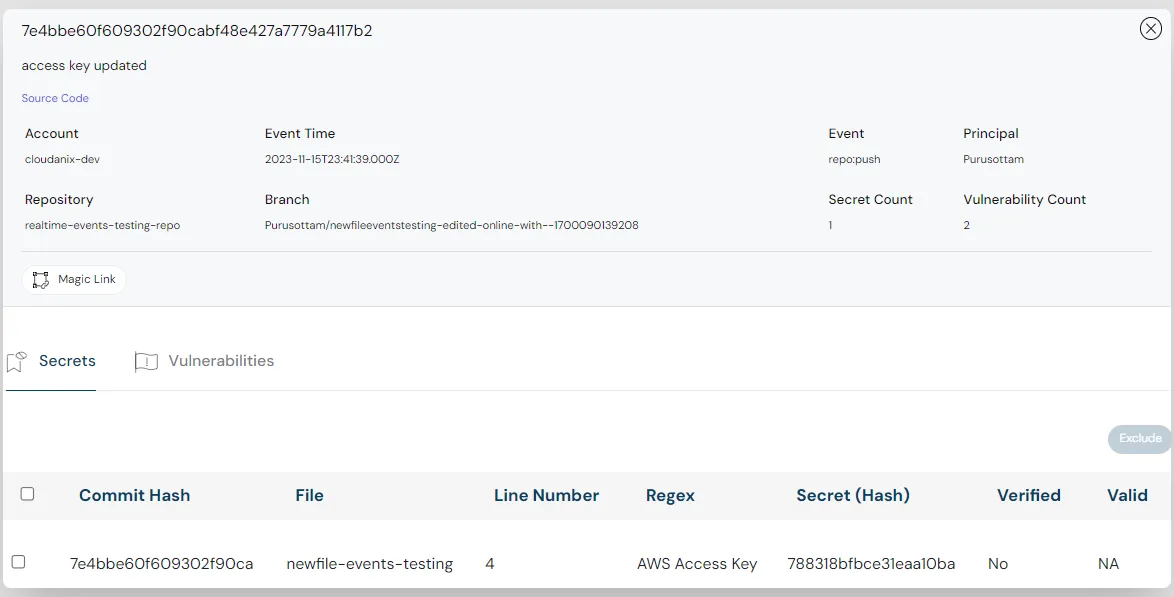
Code to Runtime
With a neat and easy-to-use dashboard, it helps developers intuitively navigate to the findings while eliminating false positives. Cloudanix starts your security journey from code all the way to cloud, including your identity management until where it runs in your workload.
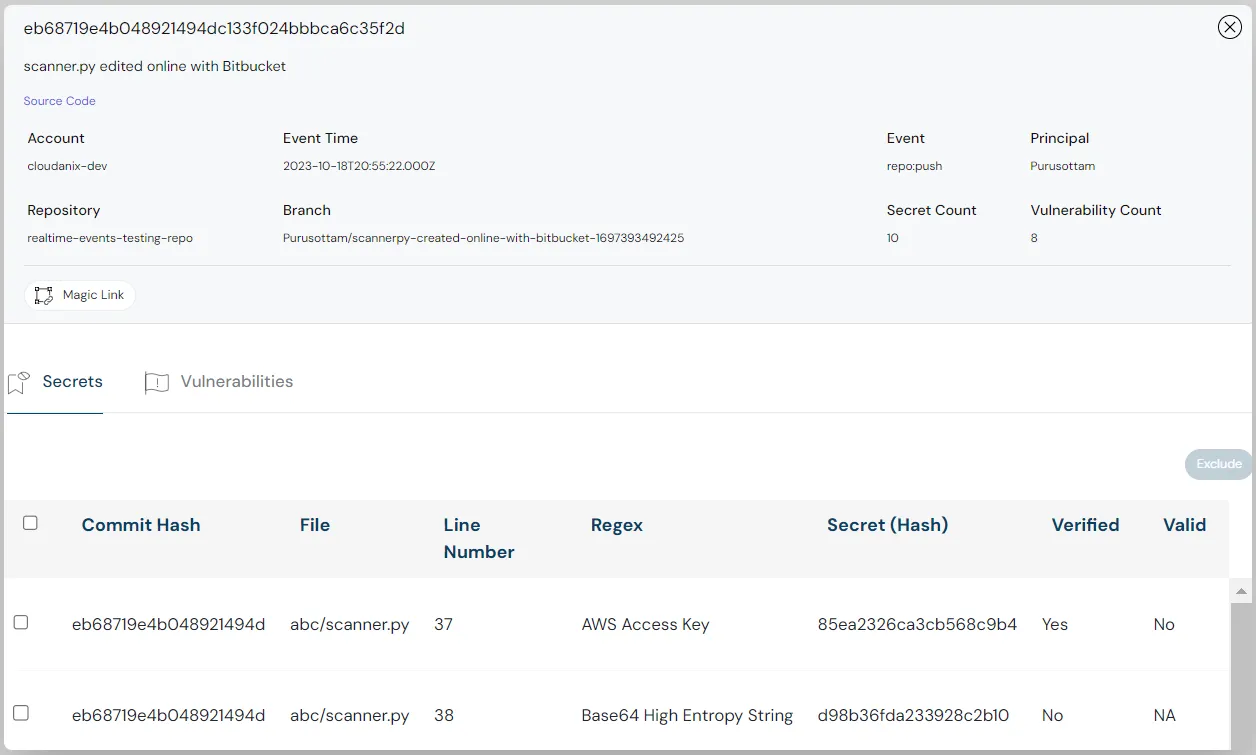
Correlation
Cloudanix also helps you connect multiple code repositories with one click and shows all the data while correlating with misconfigs, threats, vulnerabilities, checked-in secrets, etc in a single dashboard, reducing the fatigue of switching between screens. Dashboard: Security posture Dashboard: Security posture
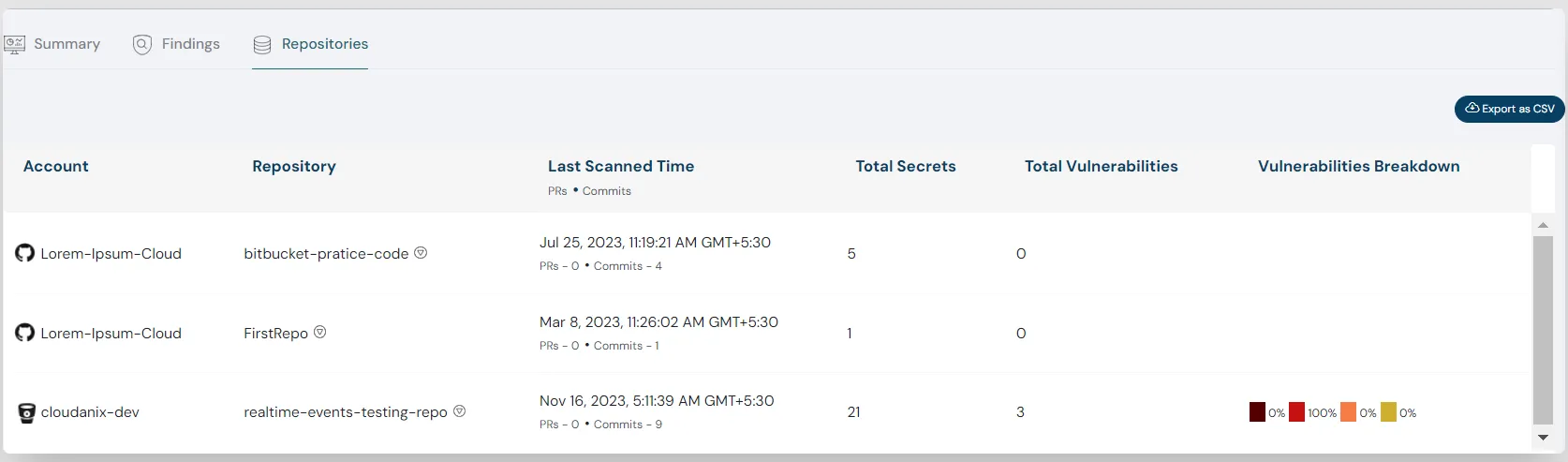
Leveraging the power of Gen AI
Delivering detailed insights and remediation recipes leveraging the power of Gen AI to ensure teams do not waste their time. Blog: Building Security Using Generative AI >
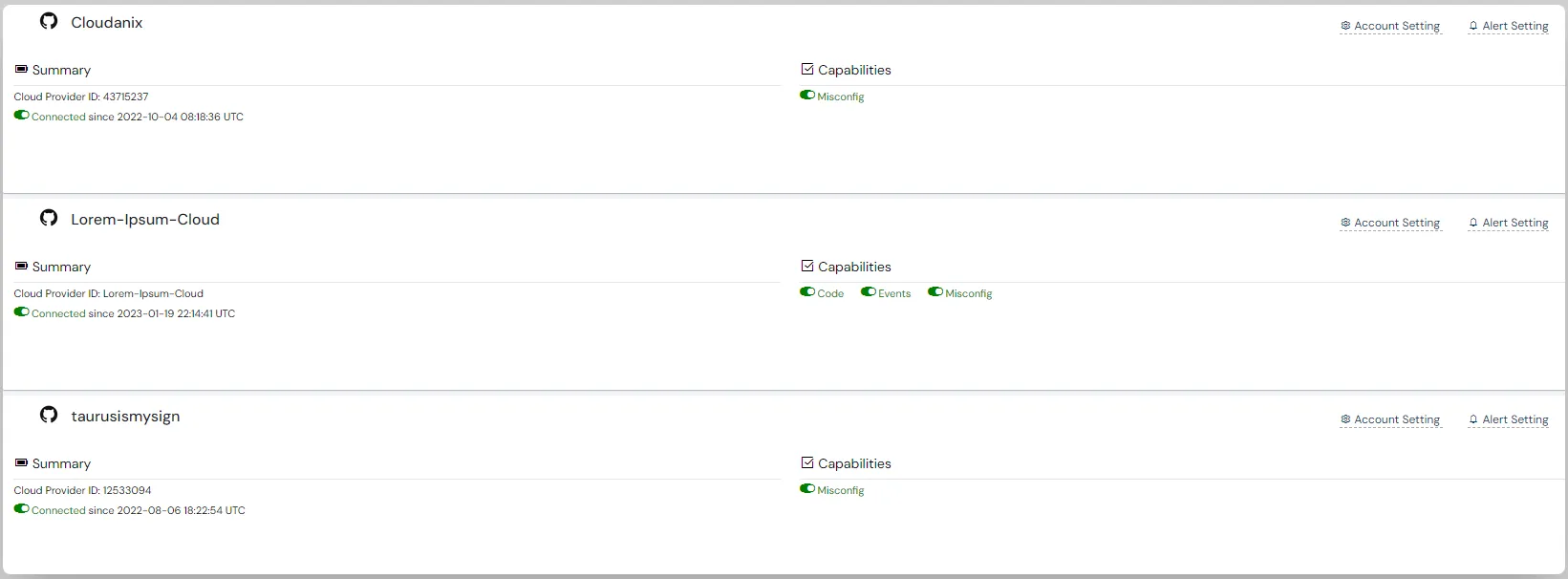
Integrations
Cloudanix integrates seamlessly with code repositories like GitHub, Bitbucket and brings all your data in one place. Cloudanix creates a productive and collaborative environment that helps teams raise JIRA tickets.

Secure Every Layer of Your Cloud Stack with Cloudanix
Unify your security workflows with Cloudanix — one dashboard for misconfigurations, drift detection, CI/CD, and identity protection.
Get StartedCLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Top 6 Azure Virtual Machine (VM) Misconfigurations To Avoid
Discover the most common Azure VM misconfigurations and how to avoid them to prevent performance or security issues.
Secure Coding
A comprehensive guide to secure coding practices, covering vulnerabilities, prevention techniques, and industry standard...

What is CSPM?
Understand what Cloud Security Posture Management (CSPM) is and how it automates security and compliance across cloud en...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...

Integrate Just-In-Time IAM Access with AWS
Dive deep into how IAM JIT and AWS Identity Center can strengthen your IAM security posture and streamline identity work...

Safeguard Identity Across Multi-Cloud Environments
IAM tools weren’t built for today’s multi-cloud environments. Learn how to adapt your identity and entitlement managemen...
Podcast
Tune in to the Cloudanix podcast for expert discussions on cloud security, compliance, and the latest industry trends. L...
