CIEM | Just In Time IAM | Cloudanix
Just In Time IAM Access For Your Cloud Teams
The IAM perimeter is the new cloud security boundary. Cloudanix Just In Time (JIT) IAM ensures that your team gets the right access only when needed—no more, no less. Boost security, reduce IAM risks, and make access approvals seamless across your organization.
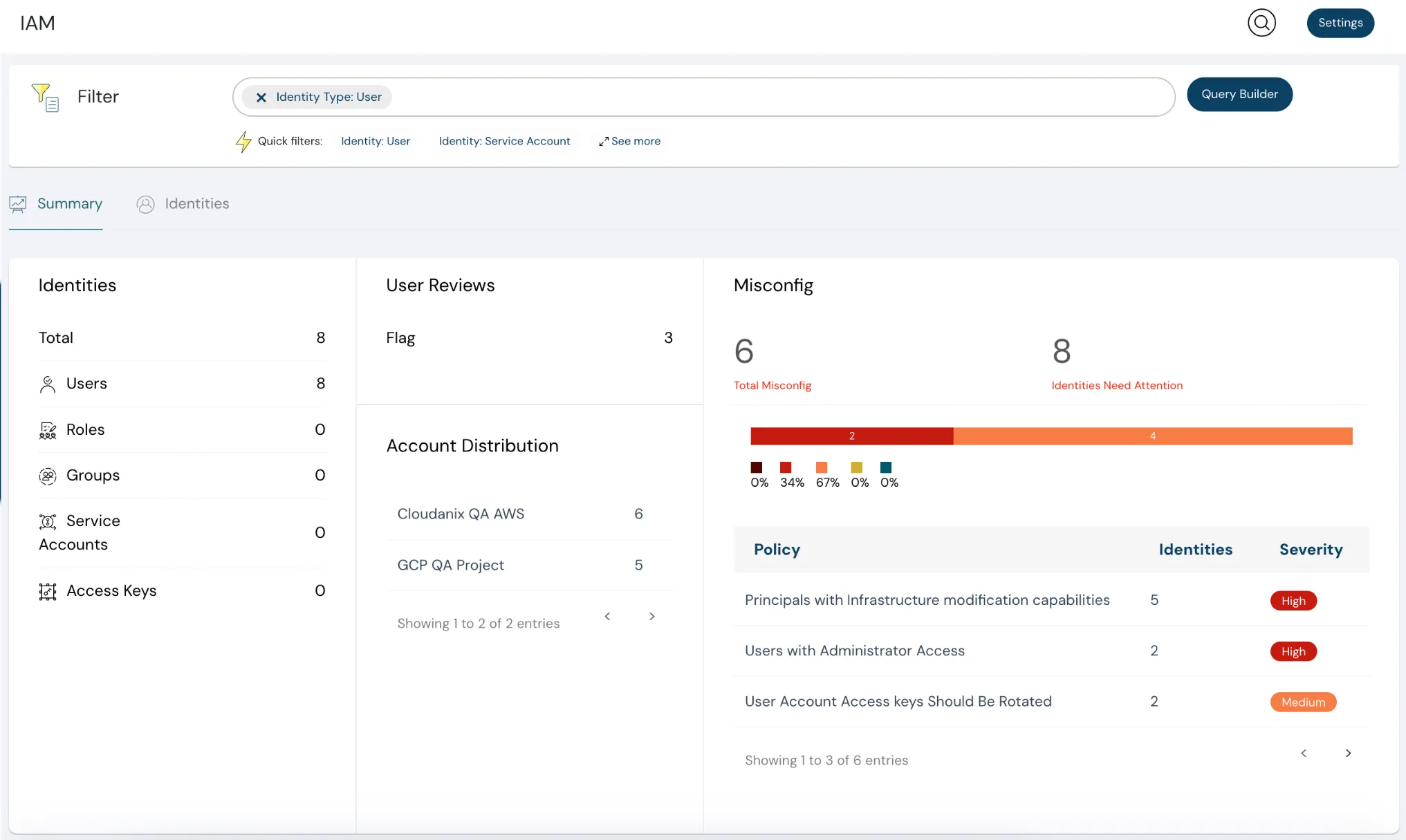
Fix IAM Toxicity With Just In Time Permissions
In the cloud, the network is no longer the perimeter—identity is. Over-permissive IAM roles create one of the largest attack surfaces in modern cloud environments. Cloudanix eliminates “always-on” permissions by granting access only when they are genuinely needed. This prevents privilege creep, reduces IAM toxicity, and strengthens your security posture without slowing teams down. Your developers get the right access at the right time, security teams get complete visibility and audit trails, and your overall cloud risk is significantly reduced. Simplified JIT Workflow Your Team Will Love — Request, approve, and audit—all in a frictionless experience. Cloudanix removes clunky request flows and replaces them with a few quick clicks for both developers and security teams.
Talk to an Expert & Get Started Today Details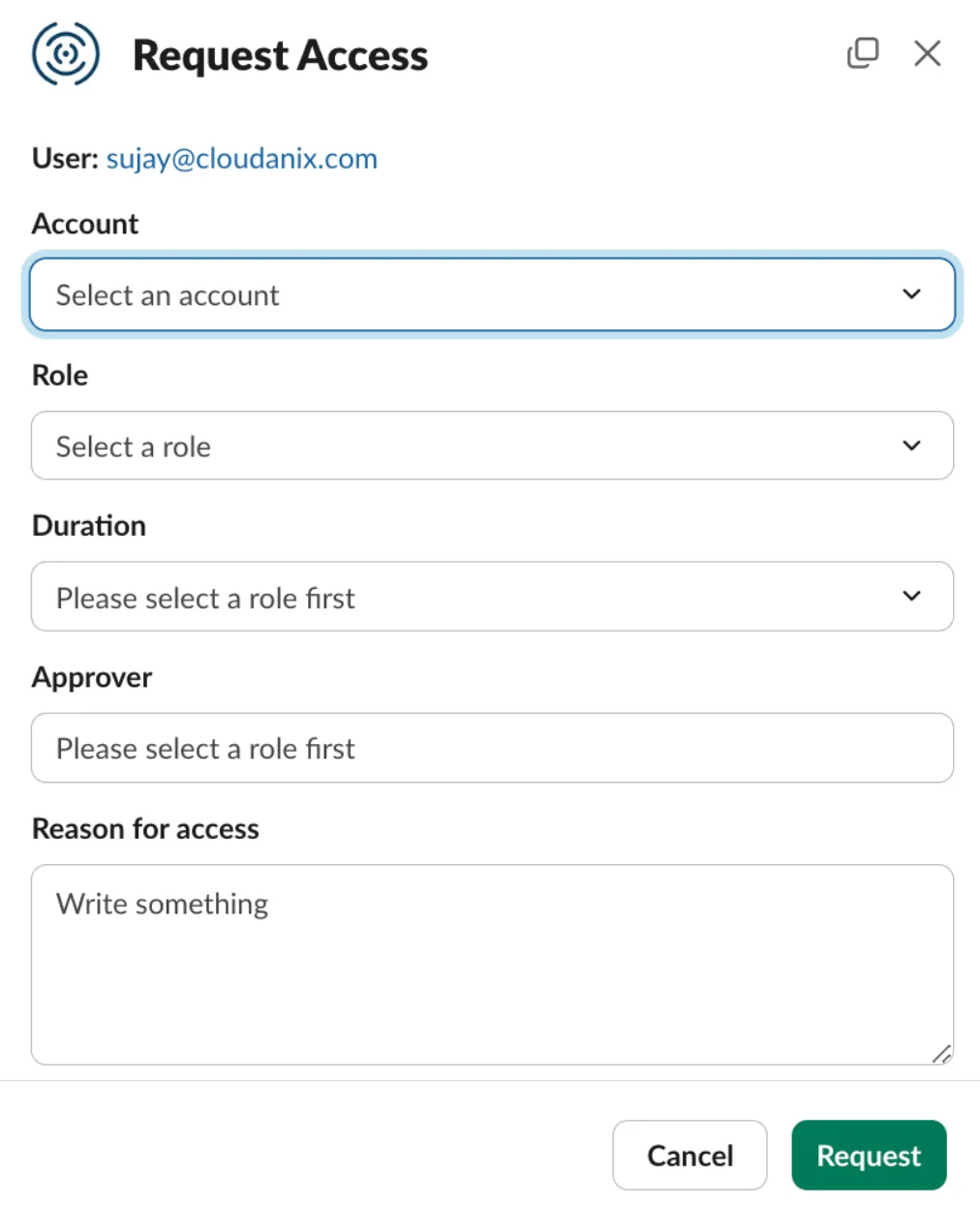
Time-Bound Access With Approvals
Team members can request temporary access for specific resources, with permissions auto-expiring once the task is complete. This ensures that no principal retains privileges indefinitely. Every request follows an approval workflow and every action is logged for compliance, enabling a healthy IAM posture.
Slack Integration For Instant JIT Approvals
JIT via Slack makes it quick to request and approve access without leaving your workflow. Simply invoke the Cloudanix JIT app in Slack, notify approvers instantly, and approve or deny with a click—speeding up access while keeping full security controls in place.
Secure Database Access With JIT
Cloudanix JIT Database access eliminates standing privileges and insecure jump boxes. Developers connect securely from their local machine to private databases via secure tunneling—no public IP exposure. All queries are logged for audit and compliance, and the process integrates seamlessly with Slack and the Cloudanix console.
Improve Security Without Compromising Speed
IAM Just-In-Time (JIT) Access
JIT access allows users to get permissions *only* when needed, reducing standing privileges and improving overall cloud security. Explore how you can integrate and implement it.
Reading Resources
Explore these curated articles and guides to better understand and implement Just-In-Time Access in your IAM strategy.
Secure Every Layer of Your Cloud Stack with Cloudanix
Unify your security workflows with Cloudanix — one dashboard for misconfigurations, drift detection, CI/CD, and identity protection.
Get StartedCLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Top 6 Azure Virtual Machine (VM) Misconfigurations To Avoid
Discover the most common Azure VM misconfigurations and how to avoid them to prevent performance or security issues.
Secure Coding
A comprehensive guide to secure coding practices, covering vulnerabilities, prevention techniques, and industry standard...

What is CSPM?
Understand what Cloud Security Posture Management (CSPM) is and how it automates security and compliance across cloud en...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...

Integrate Just-In-Time IAM Access with AWS
Dive deep into how IAM JIT and AWS Identity Center can strengthen your IAM security posture and streamline identity work...

Safeguard Identity Across Multi-Cloud Environments
IAM tools weren’t built for today’s multi-cloud environments. Learn how to adapt your identity and entitlement managemen...
Podcast
Tune in to the Cloudanix podcast for expert discussions on cloud security, compliance, and the latest industry trends. L...
