HITRUST | Risk & Compliance Framework | Cloudanix
Health Information Trust Alliance (HITRUST)
HITRUST provides a comprehensive and certifiable framework for managing risk and compliance, used by organizations across healthcare, finance, tech, and other industries. Cloudanix helps simplify shared responsibility in cloud environments, clarify control ownership, and align your security practices with HITRUST CSF.

What is HITRUST?
Founded in 2007, HITRUST (Health Information Trust Alliance) offers a widely adopted risk and compliance framework for assessment and assurance. HITRUST collaborates with experts in privacy, information security, and risk management to create a standardized yet flexible framework that applies across industries and third-party supply chains. It helps organizations manage compliance programs with clear governance and centralized documentation.
Get Started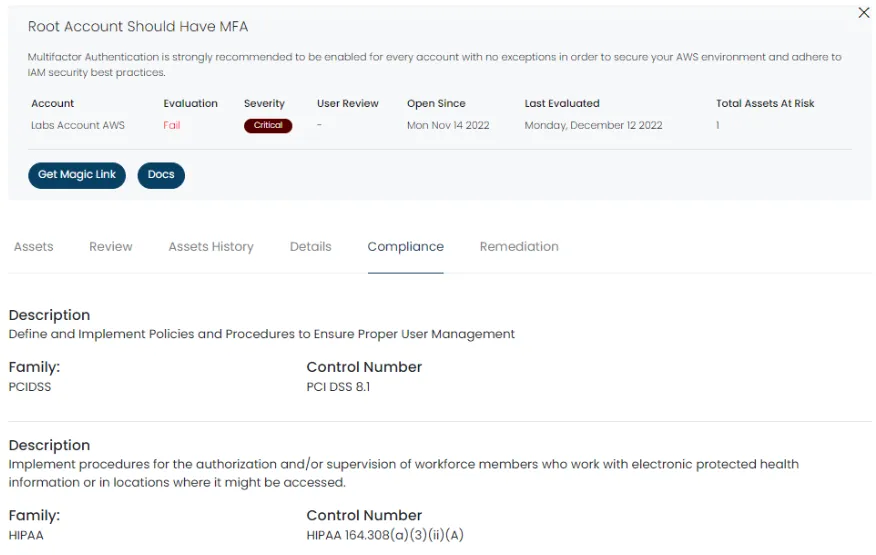
HITRUST in the Cloud
Cloud environments increase complexity around data governance, inherited controls, and regulatory clarity. HITRUST helps organizations and cloud providers define roles, responsibilities, and ownership of security controls. By clarifying shared responsibility, HITRUST eliminates confusion and aligns all stakeholders around compliance, continuous assessment, and risk mitigation.
Clarified Cloud Roles
Defines shared and inherited responsibilities between customer and cloud provider.
Centralized Risk Management
Tracks assessments, outlines corrective action plans, and benchmarks controls.
HITRUST Compliance Framework
Core Benefits and Value of HITRUST
HITRUST provides a certifiable and comprehensive security framework that integrates with global standards and scales with your business. Here’s how HITRUST helps your organization strengthen compliance and security.
Reduces HIPAA Non-Compliance Risk
HITRUST extends and strengthens HIPAA requirements, helping organizations avoid regulatory gaps and penalties.
Scalable Framework
Adapts to your organization's size, type, and complexity—whether you're a startup or a large enterprise.
Clear and Actionable Guidelines
Provides an organized, easy-to-follow roadmap for managing risk and regulatory compliance.
Evolves With You
Updates in step with your business and regulatory changes in the healthcare and security landscape.
Global Standards Integration
Incorporates existing, globally recognized standards such as HIPAA, NIST, ISO, PCI, FTC Red Flag, and COBIT.
Know moreProtection of PHI and Digital Assets
Safeguards Protected Health Information (PHI), Personally Identifiable Information (PII), and critical cloud data from cyber threats.
Regulatory Attestation
Demonstrates compliance with regulations related to sensitive data and provides a trusted certification to customers and partners.
Unified Compliance Reporting
Generate a single report that proves your organization’s security posture to all customers and stakeholders.
Lower Compliance Burden
Reduces the time and cost spent by IT teams on customer-requested compliance audits.
Partner Security Assessment
Helps you evaluate the security and compliance levels of vendors and third-party partners.
Boosts Internal Awareness
Raises company-wide awareness and accountability around compliance, security policies, and best practices.
Understand the Steps to HITRUST Certification
HITRUST Requirements Overview
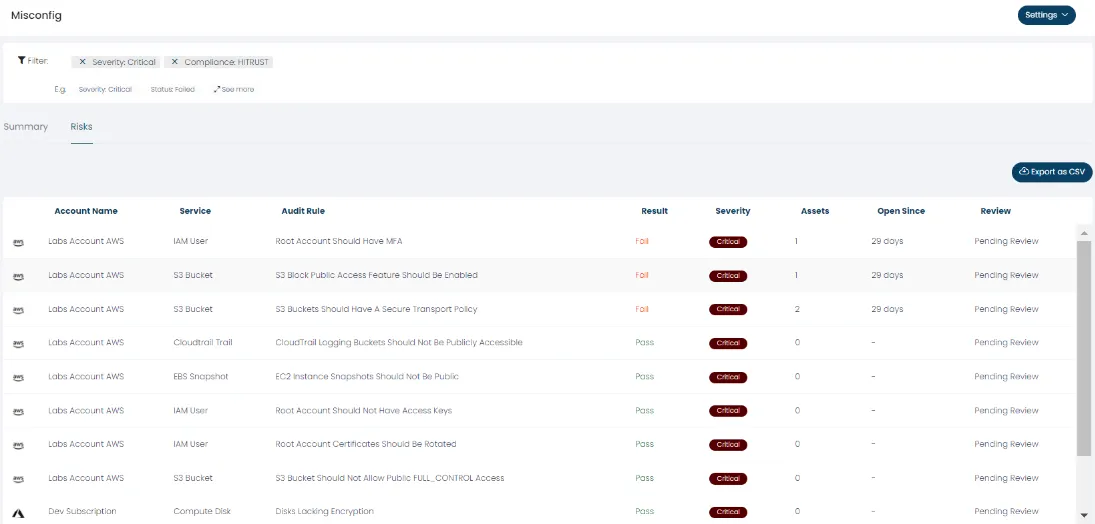
The HITRUST Common Security Framework (CSF) contains 14 control categories, 49 control objectives, and 156 control specifications—providing a comprehensive structure for organizations to manage risk and compliance. Here's how to begin your HITRUST journey, from framework download to final certification.
Steps to HITRUST Certification
A step-by-step breakdown to help you achieve HITRUST certification effectively.
- Download the latest version of HITRUST CSF.
- Outline and determine your organization’s scope.
- Purchase and onboard with the MyCSF tool.
- Perform a self-assessment based on size and risk exposure.
- Get audited by a HITRUST-authorized third-party assessor.
- Submit the validated assessment for HITRUST review.
- Receive HITRUST certification upon meeting compliance scores.
HITRUST Certification | Security & Compliance | Cloudanix
Ready To Pursue HITRUST Certification?
HITRUST Certification is a gold standard in compliance and information security. It requires time, investment, and a strategic approach—but the return is worth it. Cloudanix makes the journey easier by automating controls, visualizing risks, and aligning your cloud security posture with HITRUST CSF.
Understanding the Certification Process
HITRUST certification takes 3–4 months, depending on organizational size and complexity. It requires an external audit, an in-depth assessment, and recertification every two years. Despite the heavy lift, the benefits—reduced risk, streamlined compliance, and customer trust—make it a valuable investment. Many organizations also partner with experts to ease the process.

Why Choose Cloudanix for HITRUST
Cloudanix simplifies HITRUST adoption by mapping multiple frameworks to your environment, ensuring broad compliance and robust security. With real-time monitoring, automated threat detection, and complete asset visibility, Cloudanix reduces the operational burden while enhancing your security posture.
Secure Every Layer of Your Cloud Stack with Cloudanix
Unify your security workflows with Cloudanix — one dashboard for misconfigurations, drift detection, CI/CD, and identity protection.
Get StartedYour questions around HITRUST Compliance answered.
Frequently Asked Questions
Get clarity on HITRUST certification, how it differs from HIPAA, and who can benefit from adopting the HITRUST CSF framework.
CLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Top 6 Azure Virtual Machine (VM) Misconfigurations To Avoid
Discover the most common Azure VM misconfigurations and how to avoid them to prevent performance or security issues.
Secure Coding
A comprehensive guide to secure coding practices, covering vulnerabilities, prevention techniques, and industry standard...

What is CSPM?
Understand what Cloud Security Posture Management (CSPM) is and how it automates security and compliance across cloud en...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...

Integrate Just-In-Time IAM Access with AWS
Dive deep into how IAM JIT and AWS Identity Center can strengthen your IAM security posture and streamline identity work...

Safeguard Identity Across Multi-Cloud Environments
IAM tools weren’t built for today’s multi-cloud environments. Learn how to adapt your identity and entitlement managemen...
Podcast
Tune in to the Cloudanix podcast for expert discussions on cloud security, compliance, and the latest industry trends. L...
