CISO | Cloud Security Software | Cloudanix
Best Cloud Security Software For CISO
Visibility, Automation, and Remediation — Everything a CISO Needs to Secure Cloud Environments

What it means for a CISO
Companies now are relying heavily on public clouds to drive digital transformation. The top priority of a CISO remains the security of their cloud applications, data, and underlying infrastructure. This requires a high amount of visibility and automation — which we provide at Cloudanix to keep your cloud assets secure. You can trust us with cloud asset security and numerous other critical tasks such as: - Identity management - Misconfiguration detection - Drift management - Compliance - Cloud workload security - Remediation (automated and manual)
What you do today will shape your tomorrow
With ever-evolving cloud technologies, enterprises rely heavily on security solutions running across AWS, Azure, GCP, or Kubernetes. Cloud services and applications are the pivot for your enterprise — not just from one vendor, but from many — with multiple accounts and business apps in production. Cloudanix solves these problems today. Trusted by enterprises like Cleargene, Airgap Networks, and iMocha, our platform ensures uncompromised security. From Drift detection to IAM, Compliance, Asset Management, and Container Workload Protection — Cloudanix offers full-stack visibility with precise automated or self-serve remediation.
Proactive Drift Detection
Know what's changing and its impact — instantly.
Automated & Self-Serve Remediation
Empower your security team with quick, precise responses.
Cloud Security Software Built For Enterprise Security Leaders
How Cloudanix Helps A CISO
Cloudanix equips CISOs with the tools and insights to confidently secure multi-cloud environments through automation, visibility, and actionable remediation workflows.
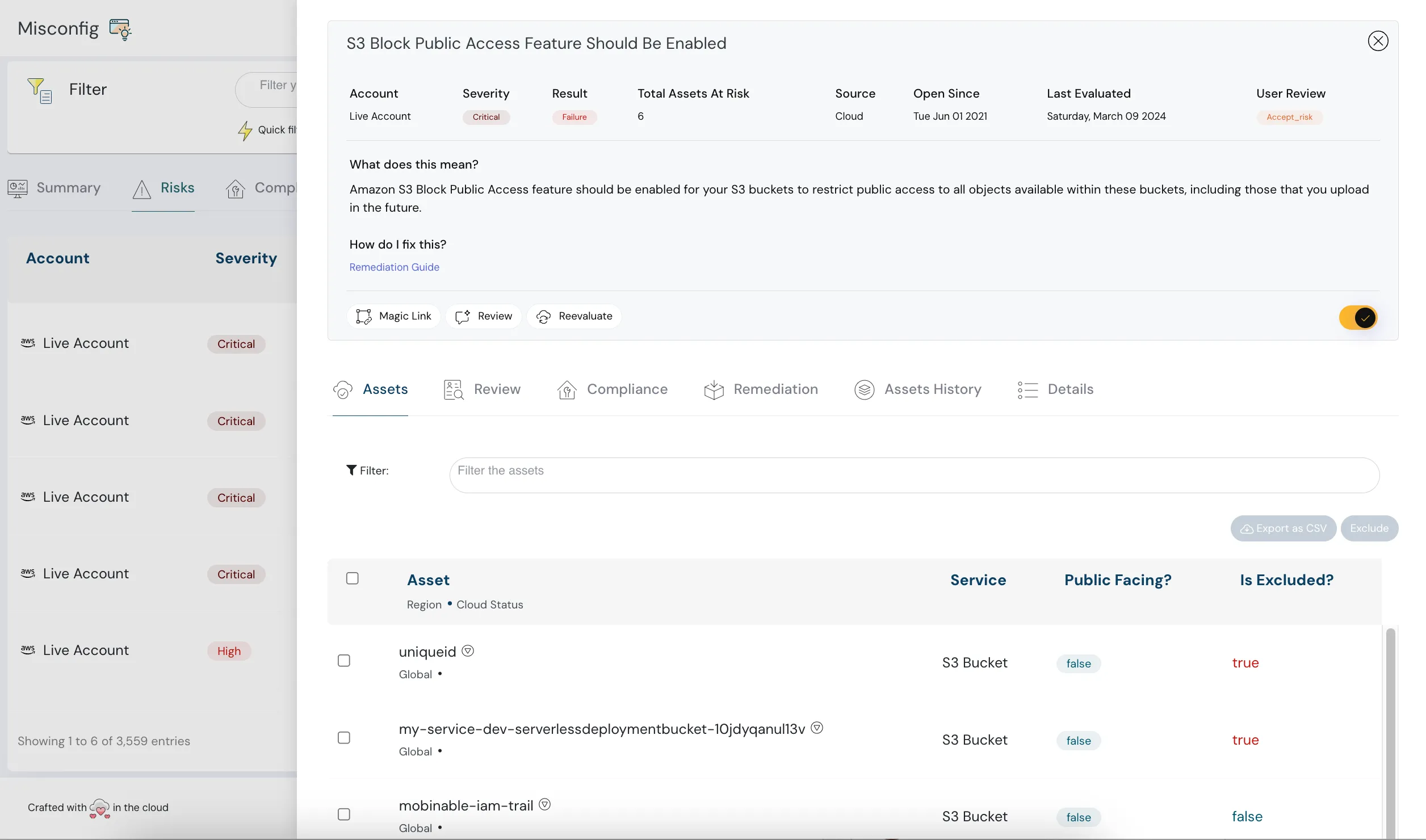
Cloud Security Posture Management (CSPM)
CSPM is the first step toward cloud visibility and misconfiguration detection. Cloudanix helps CISOs enforce compliance and eliminate drift using automated rule-based posture checks.
- Misconfiguration Detection
- Compliance Auditing
- Automated Posture Rules
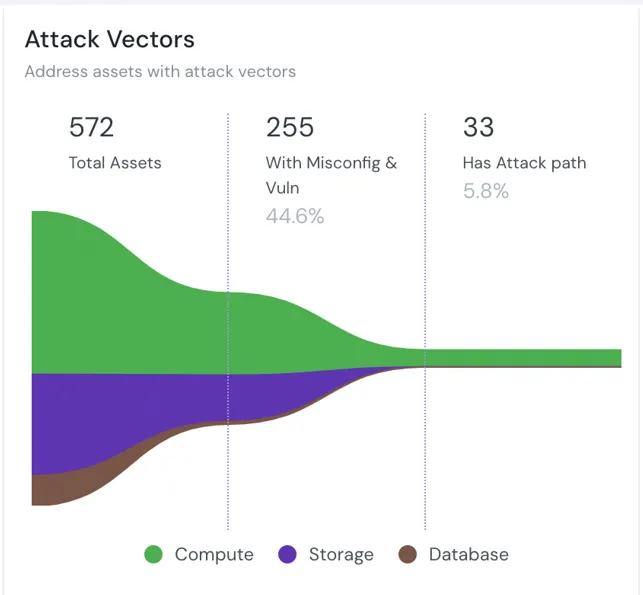
Cloud Workload Protection Platform (CWPP)
With CWPP, Cloudanix enables runtime protection of containers, Kubernetes, and workloads. This helps CISOs maintain visibility over rapidly scaling environments with low friction.
- Container & Runtime Security
- Threat Detection
- Centralized Observability
Cloud Infrastructure Entitlements Management (CIEM)
CIEM ensures that all human and machine identities are governed with least-privilege access. CISOs gain access intelligence, risk alerts, and auto-remediation workflows.
- Identity Visibility
- Toxic Permission Detection
- Automated Access Reviews
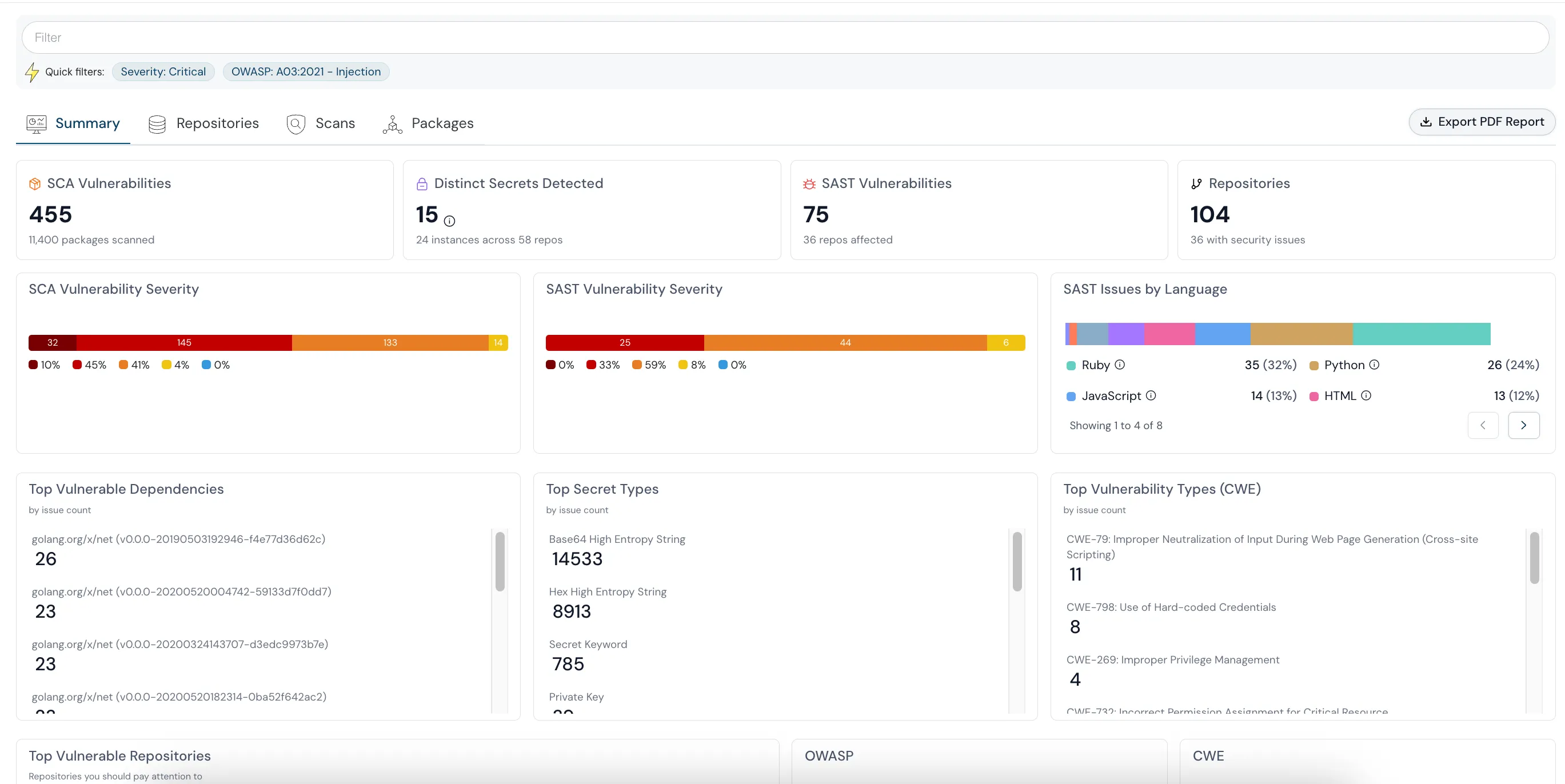
Custom Remediation Playbooks
Eliminate the fatigue of manual triage. Cloudanix allows CISOs and teams to define custom remediation playbooks and integrate automated workflows with Slack, Jira, and GitHub.
- Ready-to-Use Playbooks
- Policy-as-Code
- Slack/Jira Integration
Curated Knowledge For Strategic Security Leadership
Reading Resources for CISOs
Stay informed with essential readings tailored for today's Chief Information Security Officers (CISOs). These articles offer insights into leadership priorities, emotional intelligence, threat modeling, and organizational justice frameworks — all crucial for modern cloud security.
Recommended Reads for Security Leaders
Explore curated articles and insights every CISO should consider to stay ahead.
Secure Every Layer of Your Cloud Stack with Cloudanix
Unify your security workflows with Cloudanix — one dashboard for misconfigurations, drift detection, CI/CD, and identity protection.
Get StartedCLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Top 6 Azure Virtual Machine (VM) Misconfigurations To Avoid
Discover the most common Azure VM misconfigurations and how to avoid them to prevent performance or security issues.
Secure Coding
A comprehensive guide to secure coding practices, covering vulnerabilities, prevention techniques, and industry standard...

What is CSPM?
Understand what Cloud Security Posture Management (CSPM) is and how it automates security and compliance across cloud en...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...

Integrate Just-In-Time IAM Access with AWS
Dive deep into how IAM JIT and AWS Identity Center can strengthen your IAM security posture and streamline identity work...

Safeguard Identity Across Multi-Cloud Environments
IAM tools weren’t built for today’s multi-cloud environments. Learn how to adapt your identity and entitlement managemen...
Podcast
Tune in to the Cloudanix podcast for expert discussions on cloud security, compliance, and the latest industry trends. L...
