Cloud Native Security | CSPM, CIEM, CWPP | Cloudanix
Cloud-Native Security To Meet Modern Business Demands
Secure your modern workloads — serverless, containers, and Kubernetes — across multi-cloud environments with Cloudanix.

Why is Cloud-Native Security Important?
As businesses rapidly adopt AWS, Azure, GCP, and others — along with serverless and Kubernetes — complexity in managing security increases. Security teams are expected to support innovation while managing risks across multiple runtimes and cloud platforms. This creates blind spots and increases the attack surface for cloud-native workloads. Cloud-native security is essential to meet these growing demands and secure dynamic cloud environments from misconfigurations and unauthorized access.
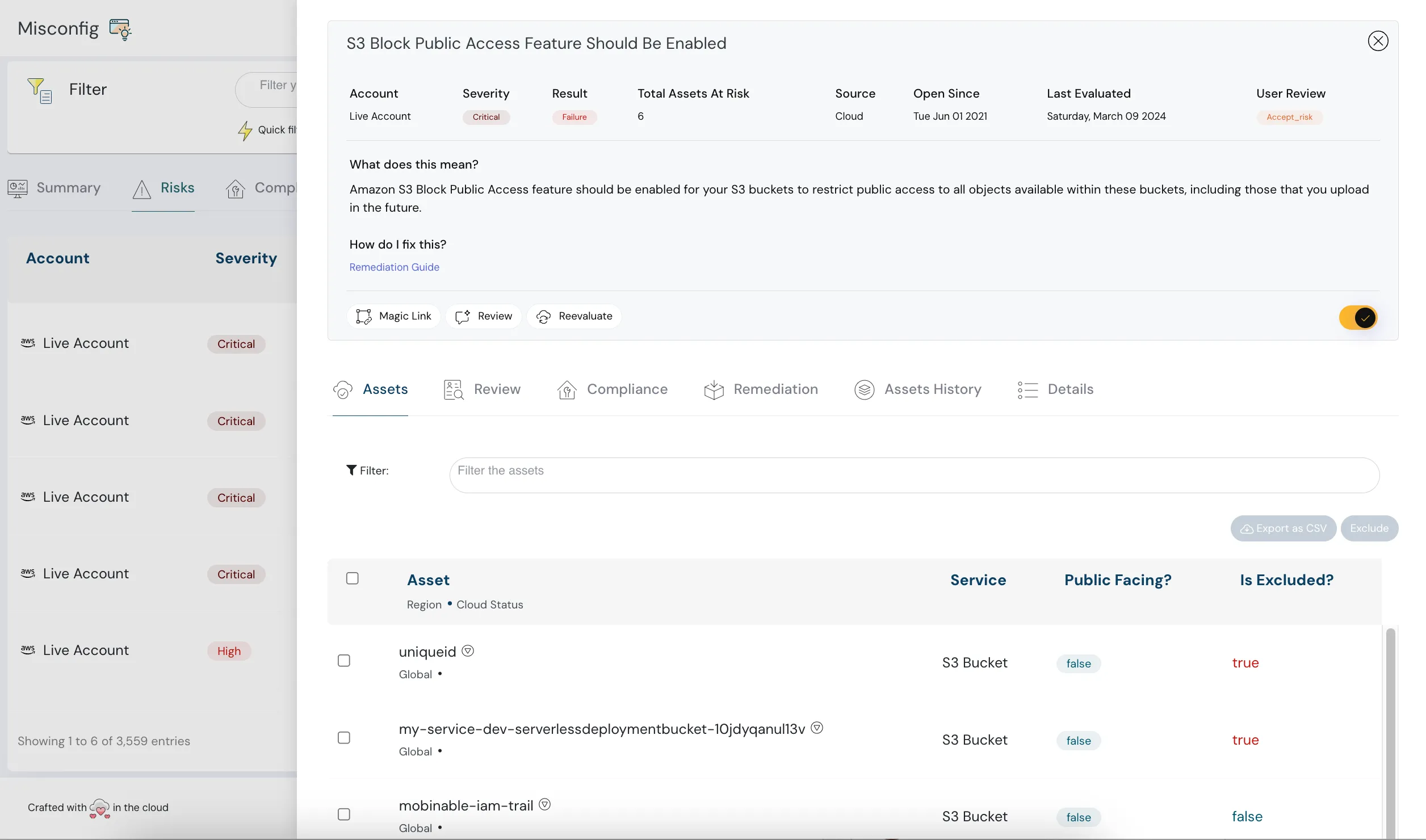
How Cloudanix Steps In
Cloudanix is purpose-built for the cloud-native world. It offers a 3-in-1 security platform (CSPM, CIEM, CWPP) to secure your infrastructure across multiple clouds and accounts — all through a single, unified dashboard. From containerized workloads to Kubernetes orchestration, Cloudanix provides the performance, scalability, and deep visibility required to detect, prevent, and respond to threats in real-time.
Multi-Cloud Ready
Secure your AWS, Azure, GCP, and more — all from a single pane of glass.
Kubernetes & Containers
Get complete visibility into workload risks across modern deployment methods.
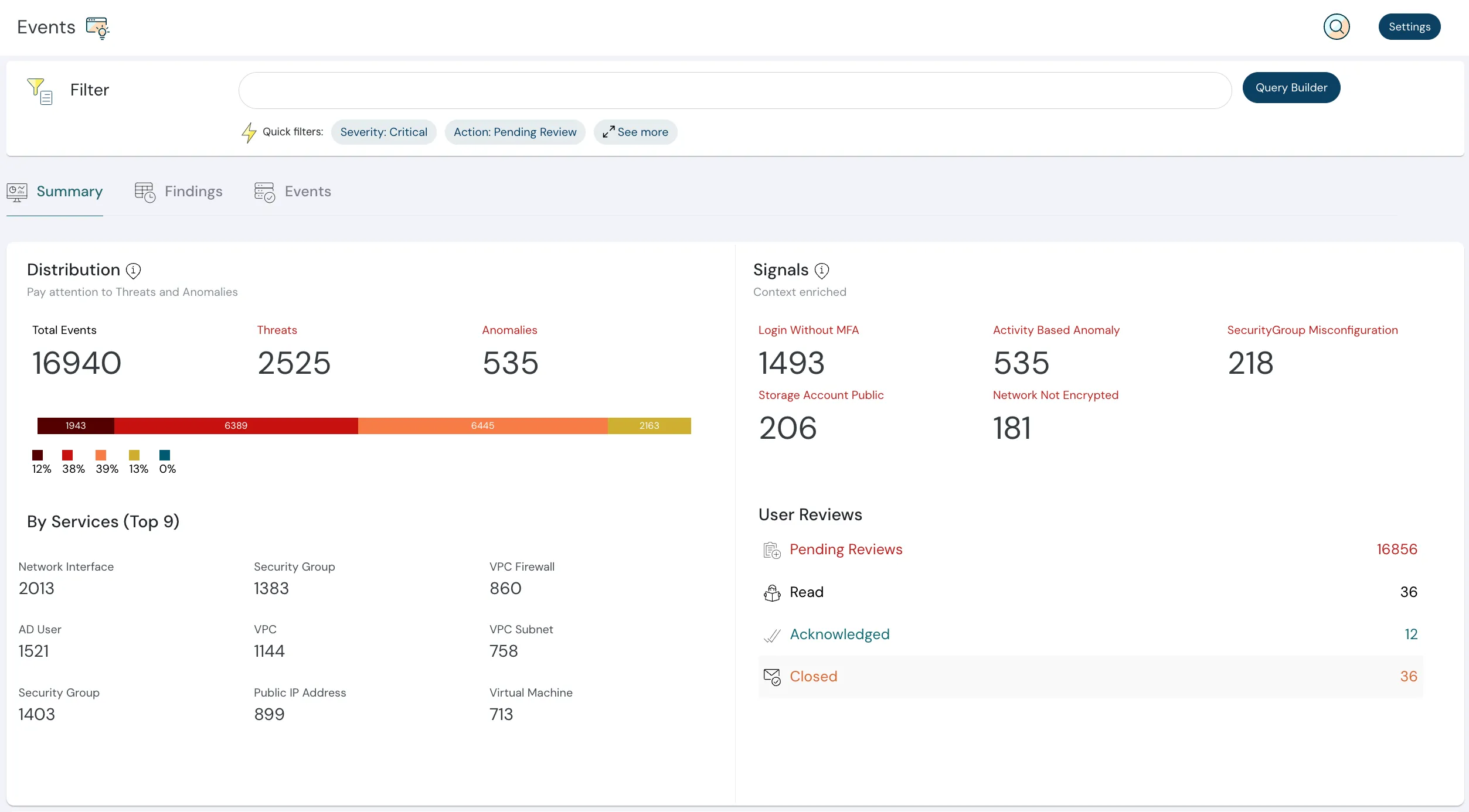
What is Cloud-Native Security?
Cloud-native security refers to the practices and technologies used to protect modern, cloud-native applications and infrastructure. These environments are distributed and dynamic, making them more vulnerable to threats. It involves proactive security strategies implemented by both engineering and cloud-ops teams to guard against vulnerabilities throughout the application lifecycle — from deployment to runtime.
You Start Deriving Value Within 5 Minutes of Onboarding
Why Should You Try Cloudanix for Cloud-Native Security?
Cloudanix helps you stay ahead of misconfigurations, compliance challenges, and real-time cloud risks across your multi-cloud environments.
Audit and Compliance
For any enterprise, Audit and Compliance is a must for stakeholder and customer trust. Meeting legal requirements is not optional anymore. Following best practices is an equally important part of compliance management. Formal regulations, laws, or internal governance controls must be aligned with standards like HIPAA, SOC 2, GDPR, ISO 27001, and more.
Drift, Misconfiguration, and Baseline
Unintentional internal oversights are one of the biggest causes of security mishaps. Without timely detection, these issues can open doorways into your cloud environment, putting your data at risk. Cloudanix provides continuous, real-time monitoring to catch drifts and misconfigurations before they cause harm.
Continuous Monitoring
Threat detection, unauthorized behavior, anomaly detection, and malicious activity are major challenges in the cloud. Cloudanix enables real-time visibility, helping you identify, prioritize, and act on threats before they escalate.
Real-Time Alerting
As cloud deployments become faster and more dynamic, the need for real-time alerts is critical. Cloudanix provides real-time alert mechanisms to notify your teams of misconfigurations and drifts. Depending on severity, alerts can be routed to multiple channels to ensure nothing slips through the cracks.
Cloud Misconfiguration Remediation
Cloudanix allows you to create custom remediation playbooks and use dozens of out-of-the-box rules to quickly secure your environment. With policy-driven automation, violations can be remediated or even prevented proactively—reducing manual work and improving cloud hygiene.
Built for Cloud Security Teams Navigating Complexity
How Cloudanix Helps Cloud Security Professionals
It’s never too early to think about security. If your answer is yes to most of these questions below, then you are ready for a CSPM tool. Cloudanix empowers Cloud Security professionals with real-time visibility, control, and automation across multi-cloud environments — all from one unified platform.
Multiple Use Cases for Cloud-Native Security
Explore how Cloudanix aligns with the most important needs of Cloud Security teams in modern cloud environments.
- Audit and Compliance mapped across several industry standards like SOC2, CIS, NIST, HIPAA and others.
- Complete inventory of human or machine identities across multiple clouds.
- Misconfigurations, Baseline and Drift Management.
- Container Security and Vulnerability Management.
- Realtime Events to keep you updated on what's going on in your Cloud environments.
Secure Every Layer of Your Cloud Stack with Cloudanix
Unify your security workflows with Cloudanix — one dashboard for misconfigurations, drift detection, CI/CD, and identity protection.
Get StartedYour questions answered.
Frequently Asked Questions
Everything you need to know about Cloud-Native Security — its differences from cloud-based models, its strengths, and the practical trade-offs to keep in mind when moving to modern infrastructure.
CLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Top 6 Azure Virtual Machine (VM) Misconfigurations To Avoid
Discover the most common Azure VM misconfigurations and how to avoid them to prevent performance or security issues.
Secure Coding
A comprehensive guide to secure coding practices, covering vulnerabilities, prevention techniques, and industry standard...

What is CSPM?
Understand what Cloud Security Posture Management (CSPM) is and how it automates security and compliance across cloud en...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...

Integrate Just-In-Time IAM Access with AWS
Dive deep into how IAM JIT and AWS Identity Center can strengthen your IAM security posture and streamline identity work...

Safeguard Identity Across Multi-Cloud Environments
IAM tools weren’t built for today’s multi-cloud environments. Learn how to adapt your identity and entitlement managemen...
Podcast
Tune in to the Cloudanix podcast for expert discussions on cloud security, compliance, and the latest industry trends. L...
