Trusted by over 100+ customers worldwide
Better Security Correlation with Cloudanix
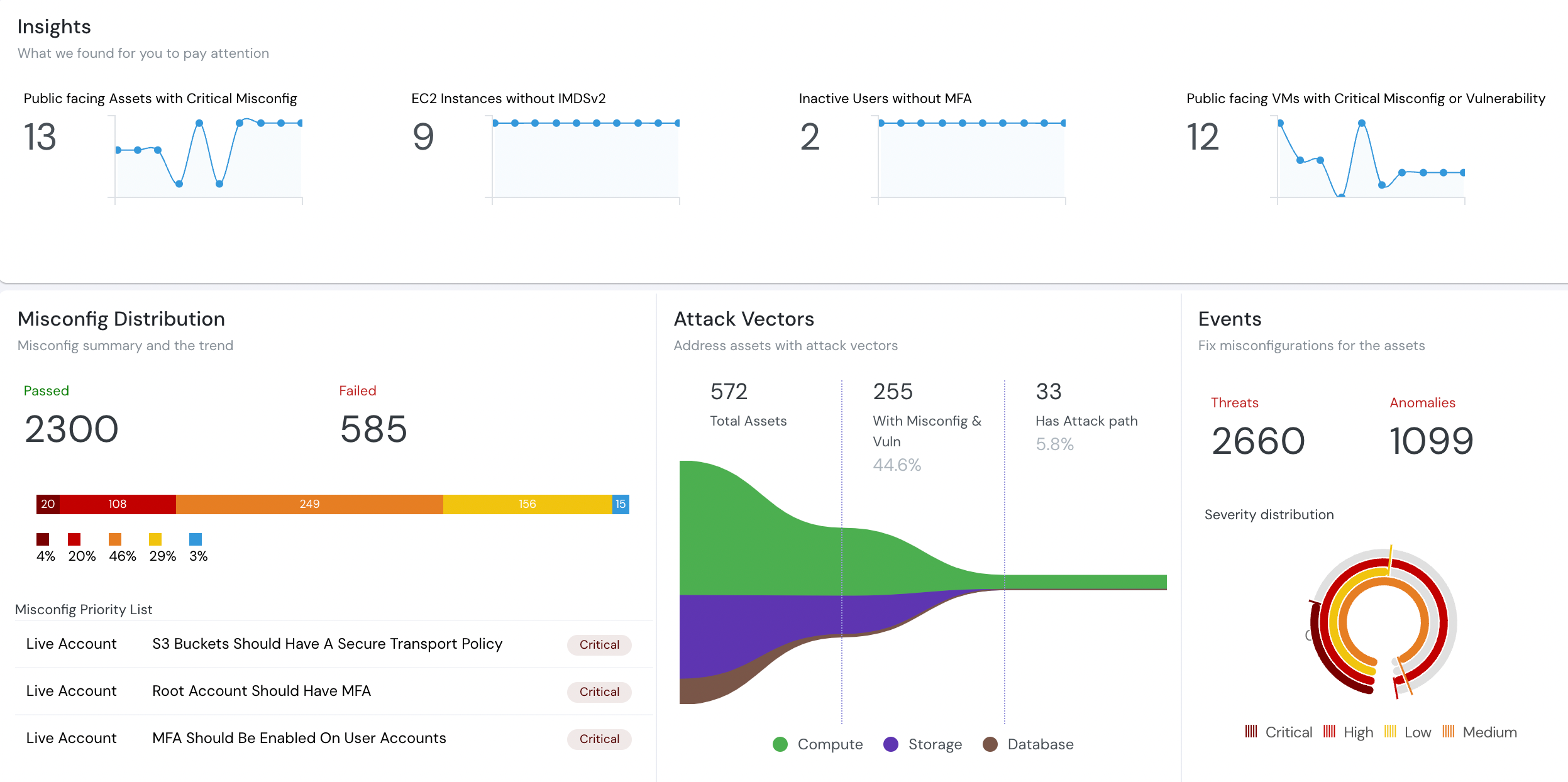
Disjointed security alerts are painful to consume. Get complete context from Code to Runtime
Code Security
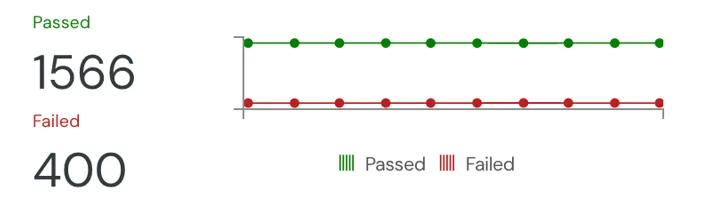
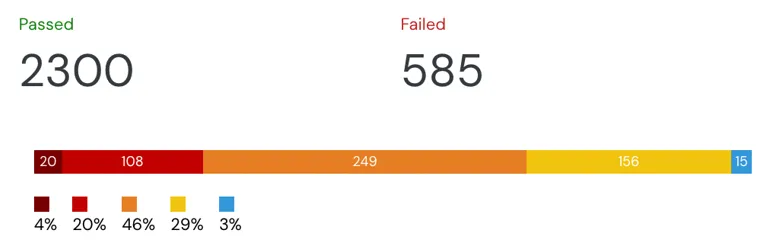
With GenAI contributing to your code writing, you need to monitor it before it reaches production. 1 click integration ensures the quality gates in your Pull requests gives the right signals to your engineers.
- Covers SCA, SAST, Secrets, CI pipelines and IaC
- Integrates with GitHub, Bitbucket, GitLab, Azure DevOps, Jenkins
- Designed for Developers, Security Engineers, and InfoSec teams
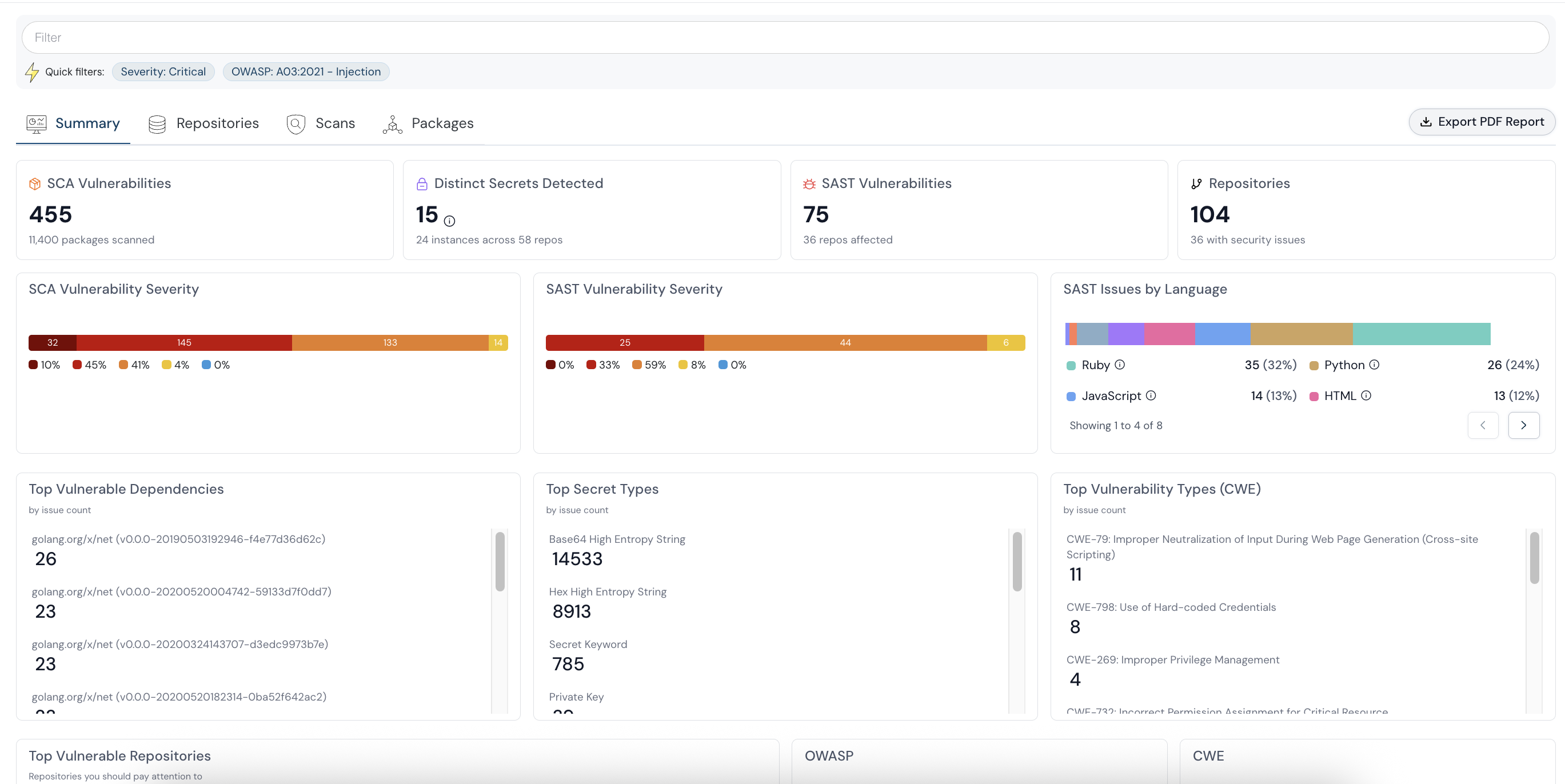
Cloud Security (CNAPP)
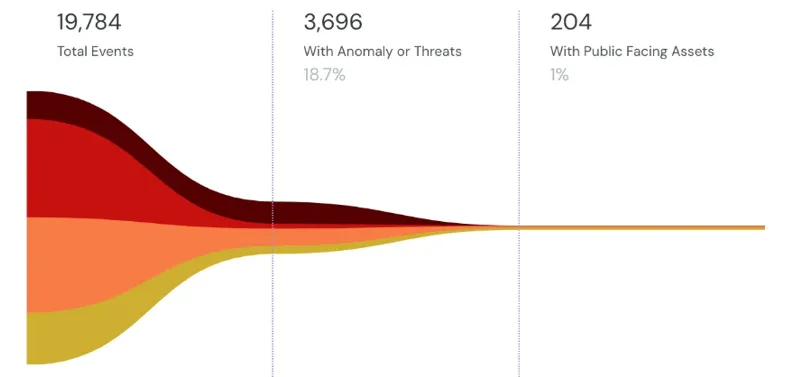
Detect and fix misconfigurations and runtime vulnerabilities. All integrated CNAPP platform ensuring your cloud misconfigurations, runtime threats, and identity risks are covered across multi-cloud environments.
- Covers CSPM, CWPP, CIEM, KSPM, Anomaly & Threat Detection
- Integrates with AWS, Azure, GCP, OCI, DigitalOcean
- Designed for DevOps, Security Engineers, InfoSec and SOC Analysts
Just In Time Access
Minimize blast radius with Just In Time access for your cloud resources. Enforce least privilege access with time-bound, approval-based access to critical cloud resources.
- Covers Cloud, Database, VM, Kubernetes access
- Integrates with AWS, Azure, GCP, any IdP
- Designed for DevOps, Data Engineers and On-call Engineers

Database Activity Monitoring (DAM)
Protect your sensitive data with real-time database activity monitoring. Policy driven capability prevents, masks data and keeps a complete audit trail for easy compliance.
- Covers any database hosted on Cloud, On-prem, or Hybrid environments
- Integrates with relational and NoSQL databases
- Designed for Data Engineers, Support, Engineering and DBA teams

Your CNAPP search ends with Cloudanix
In a world where threats can emerge from anywhere, Cloudanix stands as your ultimate defense, seamlessly integrating security across Code, Cloud, Identity, and Workloads to anticipate and block multi-surface attacks. Discover unparalleled protection that evolves with your digital landscape.
0 monitored digital assets
Co-related and contextualized for Code, images, cloud, containers, IAM.
0 secured multi cloud accounts
Cloud accounts, Code repositories, CI setup – monitored.
0 million events and threats detected
Anomalies, vulnerabilities, risk and threats – all in single pane.
Code | Cloud | Data
Why Choose Cloudanix?
Cloudanix is designed to simplify cloud security across complex environments. With agentless onboarding, built-in workflows, and customer-first support, Cloudanix ensures you not only identify risks but also remediate them effectively. From multi-cloud visibility to integrations with tools your team already uses, Cloudanix becomes an extension of your Security and Cloud Ops teams.
30-Min Agentless Onboarding
Get started in less than 30 minutes — no agents to install, no complexity to manage. Cloudanix connects seamlessly with your cloud environments and begins delivering insights instantly.
Multi* Ready
Modern environments span multiple clouds, regions, accounts, and attack surfaces (CI/CD, code, OSS). Cloudanix unifies this complexity by giving you a single security view across all your environments.
In-Built Workflows
Findings are only useful if they can be actioned. Cloudanix provides workflows out-of-the-box like creating JIRA tickets, snoozing notifications, and flagging risky permissions — making remediation faster and easier for your teams.
Support First
Our Customer Success team integrates directly with you via Slack or MS Teams. Acting like an extension of your internal Security and Cloud Ops teams, we ensure faster collaboration, guidance, and resolution.
Remediation First
Cloudanix not only highlights issues but also provides detailed runbooks and guided steps to fix them. Your team knows exactly what went wrong — and how to resolve it quickly, with minimal friction.
Seamless Integrations
Whether your team works in JIRA, Slack, MS Teams, Email, or Webhooks — Cloudanix integrates directly into existing workflows. You also get full API access to bring your own data, customize dashboards, and build tailored automation.
What Our Users Are Saying
Customer Reviews
Cloudanix is trusted by security leaders worldwide to deliver proactive, reliable, and cutting-edge cloud security.
Cloudanix completed the misconfiguration assessment of our AWS accounts even before we could fill up the subscription page with our credit card details!
The speed and efficiency of Cloudanix’s security checks have been unmatched in our experience.
We are excited to leverage the comprehensive multi-cloud DevSecOps solution by Cloudanix to secure our production workloads on AWS.
Cloudanix has demonstrated that it can solve many challenges that DevSecOps teams face, while continually adding new features such as SOC2 compliance and drift detection, which drive daily security and operational benefits.
We are a Fintech company and Cloudanix has been an absolute bliss.
It not only tells you what's wrong but also helps you fix it. Security is very crucial for us and Cloudanix, with minimal investment of our time, helps us achieve it.
Cloudanix completed the misconfiguration assessment of our AWS accounts even before we could fill up the subscription page with our credit card details!
The speed and efficiency of Cloudanix’s security checks have been unmatched in our experience.
We are excited to leverage the comprehensive multi-cloud DevSecOps solution by Cloudanix to secure our production workloads on AWS.
Cloudanix has demonstrated that it can solve many challenges that DevSecOps teams face, while continually adding new features such as SOC2 compliance and drift detection, which drive daily security and operational benefits.
We are a Fintech company and Cloudanix has been an absolute bliss.
It not only tells you what's wrong but also helps you fix it. Security is very crucial for us and Cloudanix, with minimal investment of our time, helps us achieve it.
Cloudanix completed the misconfiguration assessment of our AWS accounts even before we could fill up the subscription page with our credit card details!
The speed and efficiency of Cloudanix’s security checks have been unmatched in our experience.
We are excited to leverage the comprehensive multi-cloud DevSecOps solution by Cloudanix to secure our production workloads on AWS.
Cloudanix has demonstrated that it can solve many challenges that DevSecOps teams face, while continually adding new features such as SOC2 compliance and drift detection, which drive daily security and operational benefits.
We are a Fintech company and Cloudanix has been an absolute bliss.
It not only tells you what's wrong but also helps you fix it. Security is very crucial for us and Cloudanix, with minimal investment of our time, helps us achieve it.
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get Started