Importance of Kubernetes Security
Businesses using Kubernetes, make security a priority!
Kubernetes is often defined as a container orchestration platform that helps automate various tasks such as the deployment, scaling, and management of containerized applications. Kubernetes clusters are made up of several components, including master nodes, worker nodes, and control plane components. Where:
- Master nodes: Manage the cluster and its resources.
- Worker nodes: Runs the workloads that are deployed to the cluster.
- Control plane: Manage the state of the cluster and its resources.
Why is Kubernetes Security important?
When it comes to business or an organization as a whole, the following are the reasons why Kubernetes security is important for you:
- Kubernetes clusters are often used to run critical cloud-based applications, such as e-commerce platforms, financial trading systems, or healthcare applications. If such a highly distributed system gets compromised, a significant impact can be seen on other sides of business operations.
- Many businesses now store sensitive customer data in their Kubernetes clusters. If the security of these clusters containing this sensitive customer information is compromised, attackers could gain access to this data and steal it or use it for any kind of activity that they intend.
- Many businesses are subject to industry regulations that require them to implement certain industry security measures. For example, the Payment Card Industry Data Security Standard (PCI DSS) for protecting customer credit card data. By implementing Kubernetes security measures, businesses enable themselves to comply with these regulations and avoid fines and penalties.
- Kubernetes security is important for protecting the business’s reputation. Consider that a business experiences a security breach that is caused by a vulnerability in its Kubernetes cluster, it could damage the business’s reputation. Customers are likely to do business with a company that takes the security of their infrastructure seriously.
- Kubernetes security is important for avoiding financial losses. A security breach can cause financial losses, such as the cost of responding to the breach, the cost of lost business, and the cost of paying fines and penalties. By implementing Kubernetes security measures, businesses can cut costs on these financial losses and focus on doing business.
Kubernetes security plays a crucial role by securing different aspects of a Kubernetes cluster for businesses of all sizes. Businesses using Kubernetes, should take its security seriously and implement the necessary measures, including the applications that run on them.
What are the most common challenges of Kubernetes Security?
As mentioned earlier, Kubernetes can be complex and so does its security, and there are a number of challenges that businesses face when trying to secure their Kubernetes clusters. Some of the challenges that are faced in common are:
Vulnerabilities in container images
Container images are the building blocks of Kubernetes applications. If a container image contains a vulnerability, it could be exploited by attackers to gain access to the Kubernetes cluster or the applications that run on it.
Misconfigurations
Kubernetes clusters are highly configurable, and misconfigurations can lead to security vulnerabilities. For example, if a Kubernetes cluster is not configured correctly, it could allow attackers to gain unauthorized access to the cluster or the applications that run on it.
Lack of visibility
Complex Kubernetes clusters can make it difficult for security teams to gain visibility from all aspects of the cluster’s security. This lack of visibility leads to improper identification and remediation of vulnerabilities.
Supply chain attacks
These attacks can happen when a Kubernetes application depends on compromised or malicious third-party libraries, which attackers use to infiltrate your workloads undetected.
Runtime threats
Kubernetes applications are constantly running, which sets them open and vulnerable to runtime threats, such as malware attacks and data breaches.
Despite these challenges, there are a number of things that businesses can do to improve the security of their Kubernetes clusters.
To get started, you can follow these tips:
- Implement role-based access control (RBAC): RBAC allows you to control who has access to Kubernetes clusters and the resources they contain.
- Implement network isolation: Network isolation helps to prevent attackers from moving laterally within a Kubernetes cluster.
- Use security hardening guidelines: There are a number of security hardening guidelines that you can follow to improve the security of your Kubernetes clusters.
List of the top 10 vulnerabilities that compromise Kubernetes security
-
Insecure workload configurations
This is the most common vulnerability in Kubernetes clusters that can be caused by misconfigurations in the deployment manifests of the applications running in the cluster. These misconfigurations can give attackers unauthorized access to the cluster and its resources. -
Supply chain vulnerabilities
This vulnerability occurs when an application running in the cluster uses a third-party library with an unknown vulnerability. This vulnerability can be exploited by attackers to gain access to the cluster and its resources. -
Overly permissive RBAC configurations
This vulnerability occurs when the RBAC configuration of the cluster gives too much access to users and groups. This can allow attackers to gain access to the cluster and its resources and perform unauthorized actions. -
Lack of centralized policy enforcement
This vulnerability occurs when there is no centralized policy enforcement mechanism in place to ensure that all applications running in the cluster are compliant with security policies. -
Inadequate logging and monitoring
This vulnerability occurs when the cluster is not properly logged or monitored. This can make it difficult to detect and respond to security incidents. -
Broken authentication mechanisms
This vulnerability occurs when the authentication mechanisms used by the cluster are broken. This can allow attackers to access the cluster and its resources. -
Missing network segmentation controls
This vulnerability occurs when there is no network segmentation in place to isolate the cluster from the rest of the network. This can allow attackers to move laterally from the cluster to other systems in the network. -
Secrets management failures
This vulnerability occurs when the secrets used by the cluster are not properly managed. This can allow attackers to steal the secrets and use them to gain access to the cluster and its resources. -
Misconfigured cluster components
This vulnerability occurs when the components of the cluster are not properly configured. This can allow attackers to exploit vulnerabilities in the components to gain access to the cluster and its resources. -
Outdated and vulnerable Kubernetes components
This vulnerability occurs when the Kubernetes components are not up to date. This can allow attackers to exploit vulnerabilities in the components to gain access to the cluster and its resources.
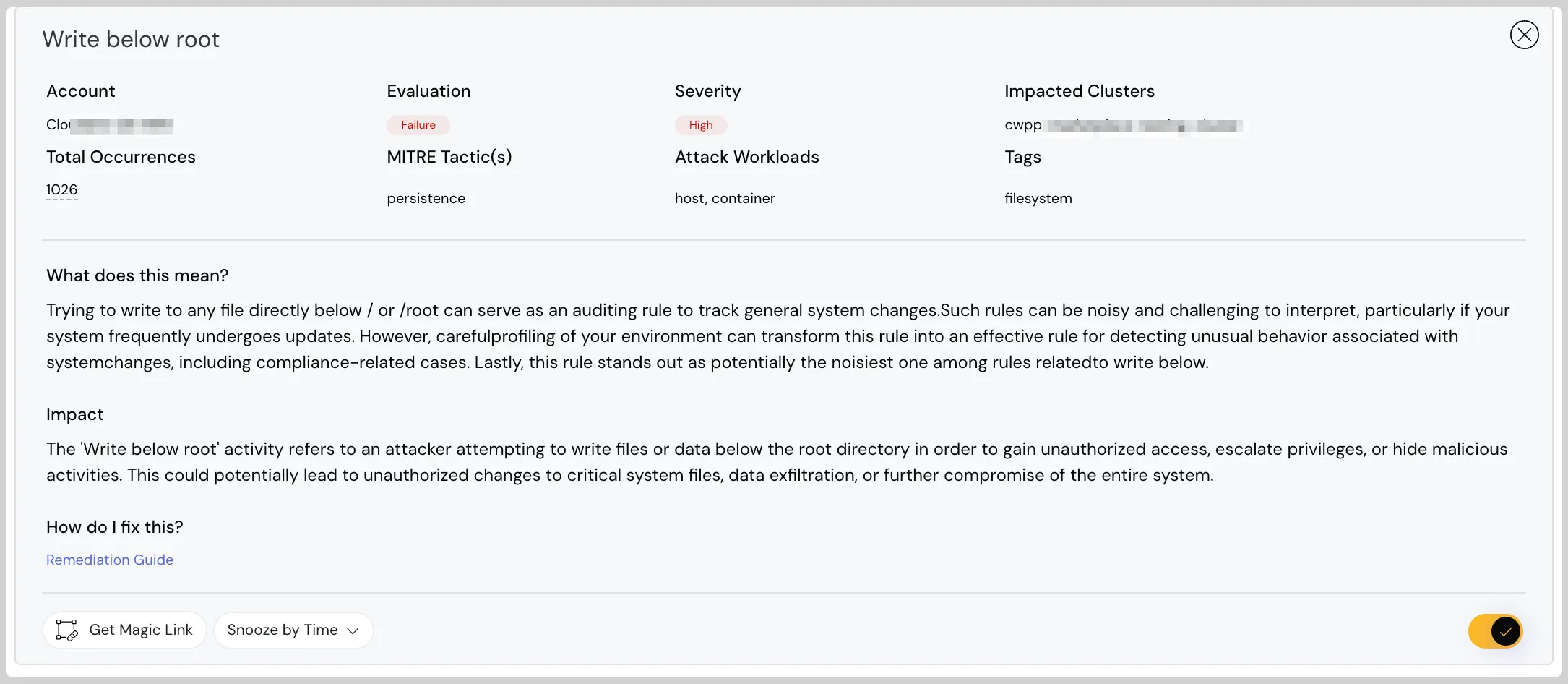
Kubernetes Metadata Enhancements
We have improved Kubernetes Policy Metadata to better map findings with MITRE Tactics and Attack Workloads, and to enhance tagging. Additionally, we’ve introduced impact analysis to help understand the severity of Kubernetes Realtime Runtime Threats.
Kubernetes Policy Metadata to better map findings with MITRE Tactics and Attack Workloads
Kubernetes and Container Security; Hand in Hand
You read that right — when it comes to the security of your cloud clusters, Kubernetes and container security go hand in hand.
Let us help you understand this analogy:
Imagine a Kubernetes cluster as a castle and the containers that run on the cluster as the people who live in the castle. Kubernetes security is like the castle walls and guards that protect the castle from attack. Container security is like the locks on the doors and windows of the houses inside the castle. Both Kubernetes security and container security are important for protecting the castle and the people who live inside.
Some of the examples to help you understand that Kubernetes security and container security are connected:
- Kubernetes security can help to prevent attackers from exploiting vulnerabilities in containers. For example, Kubernetes network policies can be used to prevent containers from communicating with a known vulnerability.
- Container security can help to prevent attackers from moving laterally within a Kubernetes cluster. For example, containers can be configured to run with limited privileges, which can help prevent attackers from escalating their privileges if they are able to compromise a single container.
- Kubernetes security and container security can be used to improve the compliance of applications that run in your Kubernetes clusters. For example, Kubernetes security can implement RBAC, a requirement of many industry regulations, such as PCI DSS and HIPAA. Container security can be used to ensure that containers are built from trusted sources and that they are running with the latest security patches.
When working together, Kubernetes security and container security can do wonders for organizations in order to protect applications that run in Kubernetes clusters from a wide range of attack vectors.
