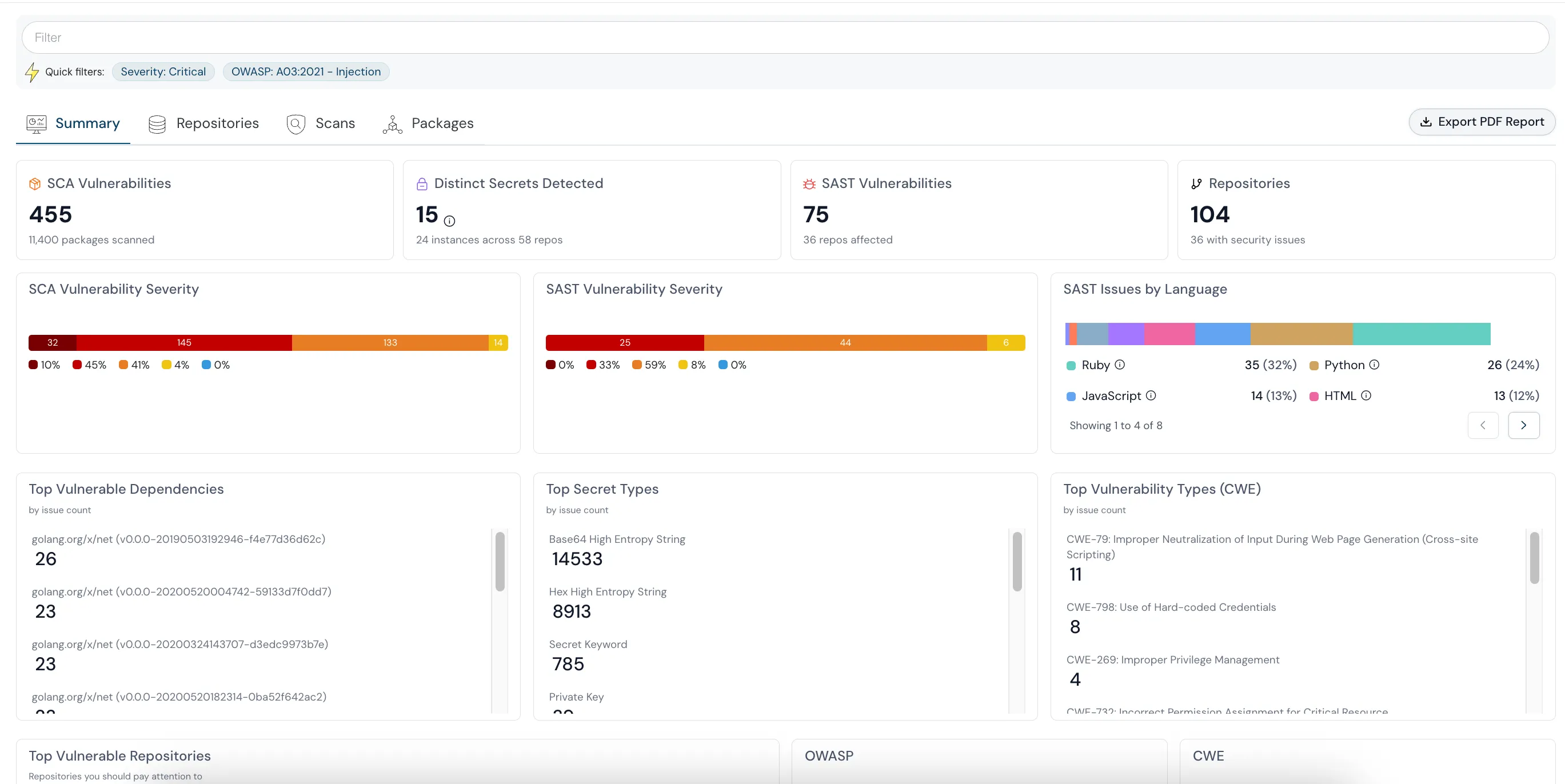
What is Code Security?
Imagine building a house using good-quality bricks, steel, cement, and other required materials with a perfect blueprint, and forgetting to lock the doors and windows when you roll out. Writing code without embedding security practices is the same.
Code security is the practice of embedding security into code. Cloud code security encompasses several use cases such as:
- Infrastructure as Code (IaC) security
- Application code security
- Software supply chain security
The primary purpose of code security is to ensure that the developed code is robust, resilient to attacks, and adheres to security best practices.
How Does Code Security Work?
We have noticed that security often comes into play only after developers have completed developing a feature, tool, or application. This shouldn’t be the case! Security and development should go hand in hand to develop a robust design that doesn’t compromise security or user functionality.
The Development Security Challenge
Consider this scenario: If companies don’t plan for encryption during their development cycle, it becomes challenging and costlier for developers to encrypt it later. Companies should build a culture where developers learn and know how to embed security in their Software Development Life Cycle (SDLC).
Core Code Security Principles
Code security should cover the following areas, which also include OWASP’s Top 10 for secure coding:
Essential Security Measures
- Preventing unauthorized access: Strong passwords and access controls
- Protecting data: Encryption and secure storage
- Preventing errors and crashes: Careful testing and error handling
- Staying up-to-date: Fixing vulnerabilities when they are discovered
OWASP Top 10 Security Risks
1. Broken Access Control
- 94% of applications were tested for some form of broken access control
- Most common vulnerability affecting web applications
2. Cryptographic Failures
- Failures related to cryptography often lead to sensitive data exposure or system compromise
- Previously known as “Sensitive Data Exposure”
3. Injection
- 94% of applications were tested for some form of injection
- 33 CWEs mapped into this category with second most occurrences
- Cross-site Scripting is now part of this category
4. Insecure Design
- Risks related to design flaws
- Focus on secure design patterns and principles
5. Security Misconfiguration
- 90% of applications were tested for some form of misconfiguration
- Often result of insecure default configurations
6. Vulnerable and Outdated Components
- Issues related to struggle in testing and assessing risks
- Using components with known vulnerabilities
7. Identification and Authentication Failures
- Previously “Broken Authentication”
- Includes CWEs related to identification failures
8. Software and Data Integrity Failures
- Focuses on assumptions related to software updates, critical data, and CI/CD pipelines without verifying integrity
- Supply chain attacks fall under this category
9. Security Logging and Monitoring Failures
- Failures directly impact visibility, incident alerting, and forensics
- Essential for detecting and responding to breaches
10. Server-Side Request Forgery (SSRF)
- Important security risk identified by the security community
- Allows attackers to make requests from vulnerable servers
4 Phases of Code Security
Code security works through four interconnected phases:
1. Prevention
Code security focuses on preventing security breaches before they occur by implementing robust measures during the development process.
2. Detection
In case of potential threats, code security practices include mechanisms to detect anomalies, unauthorized access, or malicious activities from unknown resources.
3. Response
A well-secured codebase has response mechanisms in place to address and mitigate security incidents efficiently.
4. Continuous Improvement
“Security is not a set-and-forget practice.”
Code security is an ongoing process with regular updates, patches, and improvements to adapt to emerging threats and vulnerabilities.
Benefits of Implementation
By implementing comprehensive code security measures, organizations can:
- Reduce the risk of data breaches
- Prevent misconfigurations
- Protect against ransomware attacks
- Maintain operational continuity
- Preserve organizational reputation
Code Security Tools and Techniques
While basic security hygiene can be followed manually, rigorous security requires dedicated tools and techniques. Here are popular options:
Static Application Security Testing (SAST)
SAST tools maintain a database of all known vulnerabilities that gets compared against your code.
Key Features:
- Focus on security best practices
- Scan code at different stages of SDLC
- Easy integration with IDEs and CI/CD pipelines
- Detect vulnerabilities like SQL injection
Considerations:
- Ensure the tool supports your organization’s programming languages
- Faster than dynamic testing since no execution required
Dynamic Application Security Testing (DAST)
DAST solutions use a database of known vulnerabilities but focus on the runtime behavior of your application rather than static code analysis.
Key Features:
- Tests running applications
- Language-agnostic approach
- Identifies runtime vulnerabilities
- Simulates real-world attacks
Trade-offs:
- Slower than SAST due to application execution requirements
- Better at finding certain types of vulnerabilities that only appear at runtime
Automated Code Review
With the rise of AI and Large Language Models (LLMs), automated code review is becoming popular for ensuring code security.
Implementation Tips:
- Users need to be clear about requirements and objectives
- Bridge the gap between “Clear thought and Clear ask”
- Use LLMs as a starting point for automated code review processes
- Combine with human expertise for best results
Secure Frameworks and Libraries
Frameworks provide ready-made structure and tools that help engineering teams build software more easily.
Benefits:
- Include built-in security features and practices
- Save developers time with necessary security implementations
- Provide tested and validated security controls
- Reduce common security mistakes
Challenges of Code Security
Maintaining the right balance between switching tasks, speed, functionality, and security is a delicate process. Here are key challenges:
1. Security Tools and Processes
Challenge: Too many security tools can be overwhelming.
Solution: Select tools that satisfy your needs across multiple security aspects, not just code. Integrate such tools into your development lifecycle to improve overall security posture.
2. Awareness
Challenge: Security is often treated as a separate task.
Solution: Provide continuous training and awareness so developers develop habits around secure coding practices.
3. Speed and Functionality
Challenge: Businesses cannot compromise on time or slow down their SDLC when embedding security.
Solutions:
- Maintain dedicated security teams
- Provide periodic training
- Encourage developers to identify security flaws
- Implement timely remediation processes
4. Evolution and Upgrades
Challenge: Technology evolves rapidly, increasing security complexity and attack vectors.
Solution: Developers should stay up-to-date with the latest threats and best practices through continuous learning and adaptation.
Cloudanix Approach to Code Security
The Challenge with Multiple Tools
Investing in tools that provide multi-faceted security like SAST, DAST, SCA, IAST, Database Scanning, ASTaaS, and other solutions has become common. But do you need all this complexity?
Zero Friction Philosophy
Cloudanix provides correlation right from PR to runtime!
Our Zero Friction philosophy helps us build our platform so that:
- Security teams
- DevOps teams
- Engineering teams
Stay on the same page and align from Day 1 when it comes to Code-To-Cloud security.
Key Features
Correlate Security Findings from PR to Runtime
Code is one of the first things developers create, and if not secured early on, may lead to catastrophic problems in the SDLC. Cloudanix delivers exceptional code security for your crown jewels from PR to runtime.
Container Security Integration
Comprehensive container security tools integrated into the code security workflow.
Additional Resources
Learning Materials
- Code Build Audit
- Top 10 Revised Code Security Best Practices for Developers
- Building Security Using GenAI
- Understanding the 3 Pillars of Secure Coding Standards
Product Information
Conclusion
Code security is not just about tools and processes—it’s about building a security-first culture where developers naturally think about security implications throughout the development lifecycle.
By implementing the right combination of:
- Preventive measures
- Detection capabilities
- Response mechanisms
- Continuous improvement processes
Organizations can build robust, secure applications that protect both business assets and user data.
Remember: Security is an ongoing journey, not a destination. Stay vigilant, keep learning, and always prioritize security alongside functionality and speed.
This comprehensive guide covers the fundamentals of code security, from basic principles to advanced implementation strategies. For more specific guidance on implementing these practices in your organization, consider consulting with security experts or exploring specialized security platforms.
