Principles of Least Privilege, Remove Permanent Access, Security for Docker Images in CI, and More
We’re thrilled to announce a series of enhancements designed to fortify your cloud environment and streamline your security operations. Last month, we focused on strengthening container security, enhancing identity and access management, and improving your overall user experience. From bolstering your CI/CD pipeline with Docker image vulnerability scanning to optimizing IAM permissions and streamlining notifications, these advancements are a testament to our commitment to providing you with the tools and insights needed to protect your cloud environment effectively.
Secure Your Docker Images in the CI Pipeline (GitHub Actions and Jenkins)
Fortify your CI/CD pipelines with our expanded Docker Image Vulnerability Scanning, now available for GitHub Actions and Jenkins. Proactively identify and block vulnerable images, incorporate Quality Gates, and ensure only secure code reaches production. Findings are now displayed directly within the pipeline and the Cloudanix Console, ensuring a clear view of your container security posture.
 GitHub Actions and Jenkins - Scan your docker images
GitHub Actions and Jenkins - Scan your docker images
Achieve Principles of Least Privilege for AWS & GCP SSO Setup
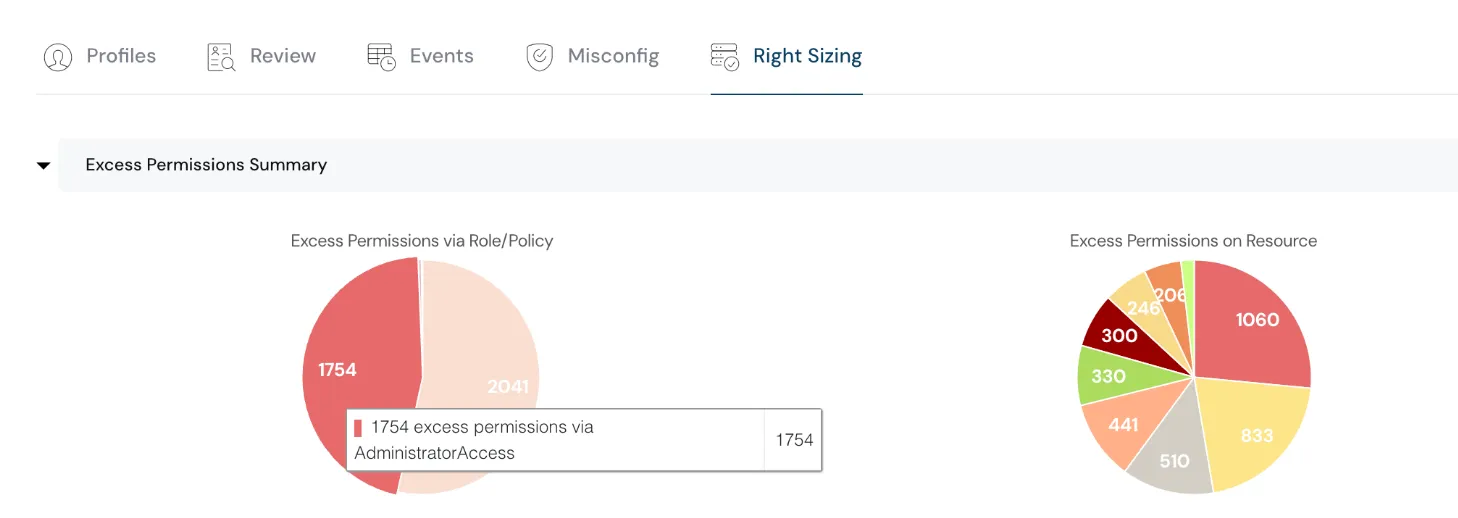
IAM Right Sizing capability has been extended to support SSO setup. Cloudanix now supports permissions assignment at AWS IAM Identity Center and Google Workspace for Right Sizing determination. This helps our customers understand over privilege, unused privilege, and make corrections to achieve the principle of least privilege. Gain granular control over user permissions across AWS and GCP, preventing over-privileged access and minimizing risk.
Know more about our Identity and Access Management capabilities >
Gain granular control over user permissions across AWS and GCP, preventing over-privileged access
Remove Permanent Access from Your GCP Environments
With this release, we have introduced support for IAM JIT in GCP — for both IAM and Workspace Users. Our customers using SSO can leverage JIT to elevate and revoke privileges for cloud users. With many levers to control the privileges being requested, such as:
- Manage JIT eligibility for roles
- Auto-approve if roles are limited in permissions
- Define maximum duration of JIT access
- And more
Elevate and revoke privileges for cloud users using Cloudanix console
Monitor New AWS Regions Seamlessly
Cloudanix can now monitor all opted-in regions along with default enabled regions. Stay ahead of emerging risks with automatic discovery and monitoring of new AWS regions, without any configuration changes.
Revamped Notifications
Our revamped notifications provide clear and actionable insights, helping you focus on what truly matters. All notifications (Daily Summary, Realtime Notifications) are redesigned to highlight the most impactful findings. With this redesign, our customers can quickly find the right context directly in the email itself.
Cloudanix Blogs
- Hiring Cybersecurity Professionals
- Emotional Intelligence from CISOs POV
- Building Security Using GenAI
- What is Zero Trust Security?
Other Resources
- Cloud Detection and Response
- Vulnerability Management and Common Misconceptions
- CyberSecurity & the Promise in India
- Designing Well Architected Systems in AWS
- Azure Entra ID and Incident Response
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Tuesday, Feb 10, 2026
The 2026 CNAPP Compliance Framework: Turning Audit from Crisis to Continuity
Introduction: The Death of the Point-in-Time Audit In the high-velocity cloud landscape of 2026, the traditional app
Read MoreThursday, Feb 05, 2026
CSPM vs. CNAPP: Navigating Cloud Security Evolution for Modern Enterprises
The shift to cloud-native architectures represents a fundamental change in how applications are designed, built, and dep
Read MoreThursday, Jan 22, 2026
Top 10 Identity and Access Management Solutions
Identity and Access Management (IAM) has traditionally been considered one of the boring parts of security. But with the
Read More