SAST, Subdomain takeover, IAM Rightsizing, Shadow admin, BYOD
Our dedicated teams have been tirelessly working delivering exceptional capabilities and features. In response to the valuable feedback received from our esteemed customers, we have significantly bolstered our investments in code security.
Continue reading to discover the remarkable strides we have made during the month of October.
Code Vulnerability Scanning
We are enhancing our code security offerings with the implementation of Static Application Security Testing (SAST). By utilizing SAST, we can thoroughly analyze your source code to identify any potential security vulnerabilities right from the start, even during the PR process. This, combined with our secret scanning capabilities, will grant you a greater level of visibility into any code issues that may arise.
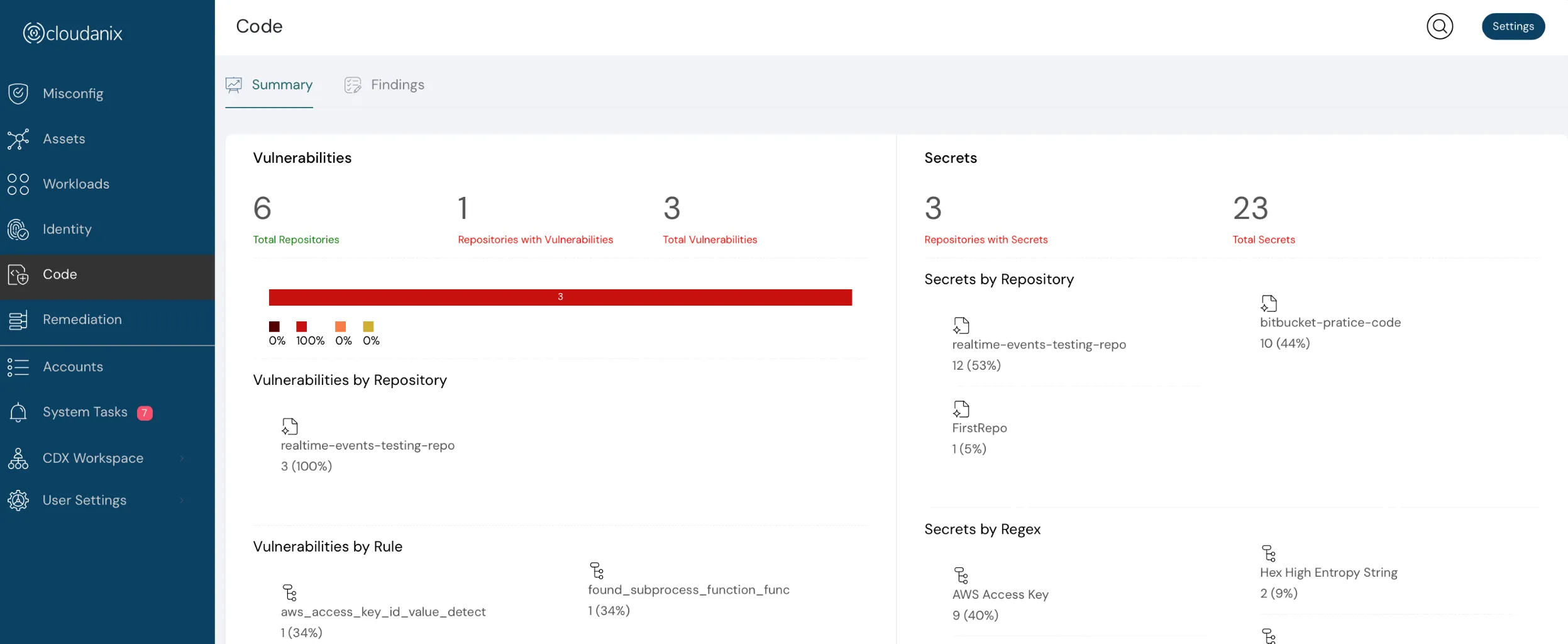
Code Vulnerability scanning dashboard
 Holistic view code scans
Holistic view code scans
 List of vulnerabilities with details
List of vulnerabilities with details
Subdomain Takeover Validations
Protect your subdomains from potential hijackers. With Cloudanix’s advanced capabilities, we can identify these risks and provide effective remediation strategies to keep your domains secure.
 List of available risks with remediation
List of available risks with remediation
IAM Rightsizing for AWS & GCP
Cloudanix conducts a comprehensive analysis of permissions for all IAM principles, identifying both utilized and unused permissions. Our solution then assists in optimizing and aligning these permissions to adhere to the principles of least privilege, ensuring the perfect fit for your organization.
Malicious IP Detection
Introducing Cloudanix’s capability to identify and thwart malicious IP activities within your cloud environments, seamlessly integrated into our Events monitoring feature.
Global Search with Identity Data
Discover the power of our enhanced global search feature, now with Identity Information! Easily search for any IAM principal and uncover their privileges and misconfigurations, all conveniently in one place.
 Global search feature including Identity data
Global search feature including Identity data
IAM Shadow Admin Detection
Our enhanced IAM Policies now have the ability to detect shadow admins, individuals who can manipulate their privileges to gain admin access and potentially seize control of the account.
Bring Your Own Data (BYOD)
Bring your security findings from external sources. Now, enjoy seamless integration with GuardDuty out of the box.
 Bring your own data at Cloudanix
Bring your own data at Cloudanix
Explore these features here
Additional Resources
- What is Identity and Access Management?
- How to go about building a SAST plan for your company?
- What is Vulnerability Management?
- What is Code Security?
Industry News
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Tuesday, Feb 10, 2026
The 2026 CNAPP Compliance Framework: Turning Audit from Crisis to Continuity
Introduction: The Death of the Point-in-Time Audit In the high-velocity cloud landscape of 2026, the traditional app
Read MoreThursday, Feb 05, 2026
CSPM vs. CNAPP: Navigating Cloud Security Evolution for Modern Enterprises
The shift to cloud-native architectures represents a fundamental change in how applications are designed, built, and dep
Read MoreThursday, Jan 22, 2026
Top 10 Identity and Access Management Solutions
Identity and Access Management (IAM) has traditionally been considered one of the boring parts of security. But with the
Read More